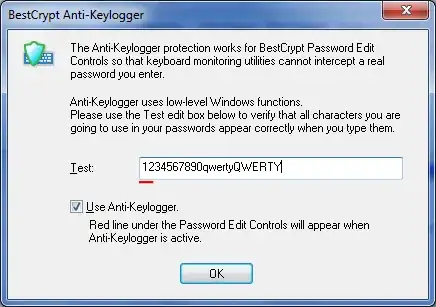
I do own Kaspersky Internet Security (KIS) and BestCrypt Volume Encryption (BCVE) (unrelatedly) and both offer some mechanism (KIS) to "protect my passwords while I enter them". Kaspersky primarily does it when I use my browser while BCVE offers this only when entering the password that protects data volumes.
Also Kaspersky's solution doesn't really change any behavior in any way that I could notice while BCVE effectively blocks my password manager (KeePass) from entering the password for me. A similar strange behavior applies when I enter the self-protection password for Kaspersky to change its settings.
So my question is now:
How does (/can) this password protection "technology" work (conceptually)?
The only (ways) I can imagine this works is by temporarily disabling the keyboard hook system in Windows as well enforcing the clipboard to be empty, but I think they do more (in a clever way).