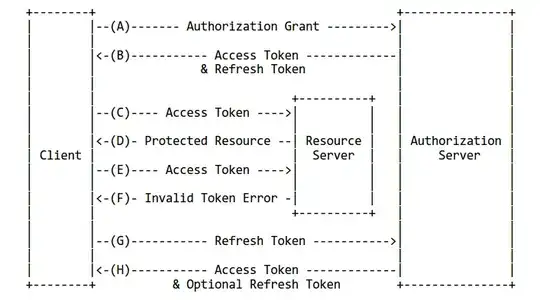
I'm building an oauth 2.0 protocol. I'm wondering how the refresh token works exactly.
My understanding is that the use of a refresh token enable short lived access token and therefore limits the vulnerability of those access tokens. Great so far. Once an access token expires, you somehow use the refresh token to get a new access token.
I'm wondering how that last part happens exactly (without interrupting the user flow by logging them out):
- to secure the transaction, should it be required that the app id and app secret are sent along the refresh token, to ensure the identity of the requester?
- if so, it sounds like you don't want to store an app secret on a client (web or mobile app or other) so how can you do that without logging out the user?
- if not, what is the point of the refresh token if you can't use it to verify the requester identity? And is it ok to store the refresh token in a client?