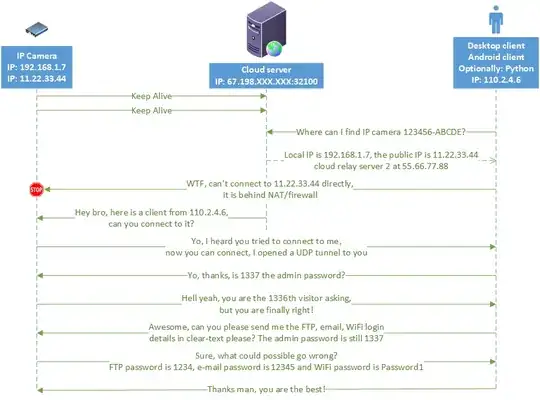
I keep reading about hackers accessing laptop and home security camera systems. Most home users are using SOHO routers meaning they are on a private IP range behind a NAT. I realize NATs aren't designed for security, but if an IP camera is behind one, how can a hacker access it?
Would it require either the camera's software or the router to have a security hole (0 day, bad code) or end-user misconfiguration (weak/default password, open/mapped ports) that would let the attacker in?