Is that more or less like visiting the website by typing the hostname into your browser and letting it load?
Short answer, no ... it's not even close.
When you run whois you are doing a lookup of an IP or Domain's publicly registered information. In many cases the whois request will not even communicate with the target server. Rather whois databases are mainly run by registrars and registries. ICANN’s IANA department runs the central registry for all kinds of Internet resources, pointing to the whois server of the responsible (sub)-registry as well as the contact details of this registry.
The program you are running is also running a ping against the server. In most cases the standard ping command makes use of ICMP or The Internet Control Message Protocol. This however is not always the case for programs that are checking the status of a server. The tool you are using might instead be doing a port scan to check the availability of ports 80 and 443. NMAP is an example of another tool that has this functionality.
Now, to the heart of your question ... how are all of the things listed above different from visiting the website itself? The answer is that all of the tools above are pretty simplistic, they send a message and get a message but do very little processing. They are all more or less dumb challenge/response type systems in comparison to opening up a TLS socket for communication via HTTPS.
When you open your browser and navigate to https://google.com, the following things happen:
- Your browser does a DNS lookup of
google.com in an attempt to get an IP address to which it should connect.
- Once an IP address has been obtained, a TLS socket will be negotiated:
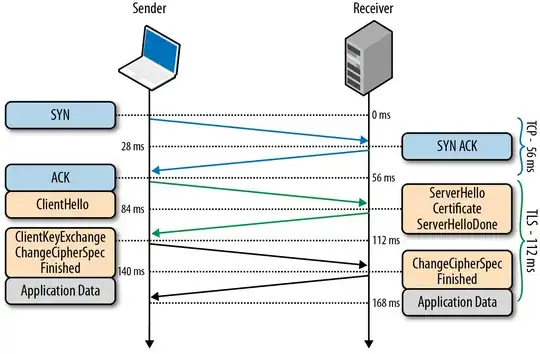
- After a secure socket connection has been established, the browser makes a HTTP:GET request for google.com's
/ (usually a file called index.html but can also be index.php, index.asp, etc depending on the server).
- Once the HTML content of
/ is received by the browser, it attempts to load its content for you to see ... however while the HTML can have images (base64 uri encoded) and scripts in its content ... it usually contains references to other files that need to be downloaded as well. In many cases loading a page can result in a great number of secondary requests ... for example loading google.com caused 12 different HTTP requests.
- Once the page is loaded, any JavaScript is then interpreted and client side code is executed within your browser ... this JavaScript code or flash / java-applet code is usually the root cause of the malicious activities you are afraid of.
It is possible to load a page without JavaScript by using something like NoScript however, this could also prevent the web page from functioning ... for example you wouldn't be able to log into stackexchange without letting some of the JavaScript content be executed.
So to answer the heart of your question, no ... it is very unlikely if not totally impossible to infect your computer by running a whois or ping against evil-website-of-doom.com ... however, if you ping it ... they will get your IP address which may or may not be an issue ... but that is a different question completely.
