Don't be sure that you digitally signed the document. Adobe Reader and related products also include echoSign features. EchoSign is an electronic (not digital) signature system.
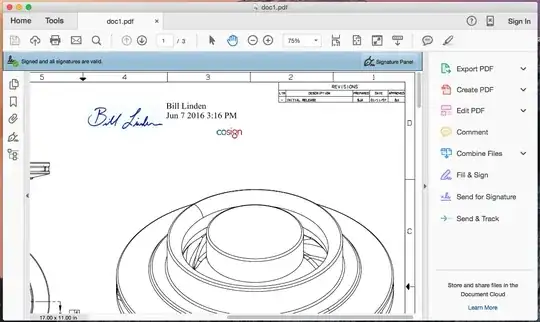
If you still have the "signed" PDF, then open it in Adobe Reader. If you see a colored bar across the top that includes a button for the "Signature Panel," then the PDF is digitally signed.
In that case, open the Signature Panel (use the button) and see what it tells you about the document’s signature(s). The screenshot below shows a digitally signed PDF opened in Reader
Added Re your questions:
What crypto lib was used?
[Adobe Reader is a huge piece of locally installed sw. So it would not be a big deal for it to either use an OS crypto lib or include one for platforms that don't have what it needs.]
The person receiving this document does not even have my public key; how do they know it is me who filled it out? Does the document get sent along with my public key?
[Yes, digital signatures include a copy of the public key of the signer. However having the public key of a signer does not establish trust, as you mention. Trust is established by having a trust relationship with the key that signed the signer's key.
If a public/private key pair are being created on the fly locally on the signer's machine then they are most probably self-signed. In that case, there is no way for the relying party (recipient) to have a pre-existing trust relationship with the signer's key since it doesn't have an issuing parent that guarantees it.
The recipient can manually establish a trust relationship with the signer's key if desired.]
In case the public key does get sent along with the document, there would still be no mechanism to associate the key with my identity (in the same way a CA would do it). So what benefits exactly does this kind of signing provide?
[You're confusing the availability of a public key with the potential trust relationship from a CA or someone else who issued the key.
- Digital signatures include the public key of the signer.
- The signer's key can be self-signed. In that case, the digital signature ONLY guarantees that the document has not been changed since it was signed. And even that guarantee is weak since you can't easily tell if someone else has impersonated the original signer and changed the document.
- If the signers key was issued from another key (either one that is chained back to a CA, or one that is chained back to an organization's master key), then there you can create a much stronger case that the key should be trusted. In addition, if the key is chained back to a key that is already pre-trusted by your software (Reader), then the sw can automatically verify the trust relationship between you and the signer.)
Bottom line: self-signed digital signatures should be avoided by anyone serious about their signature. Self-signed signatures are easily forged by someone else since there is no possibility of having a trust relationship with the key's issuer since there is no issuer, per se. The key guaranteed itself.
Last comment: for a digital signature to be strong, its private key must be stored in a Secure Signature Creation Device such as a tamper-proof appliance or a smart card. Storing the private key on a regular computer or server is very weak beer and does not provide a legally binding signature in many use cases around the world. (But is fine in other use cases.)
]
