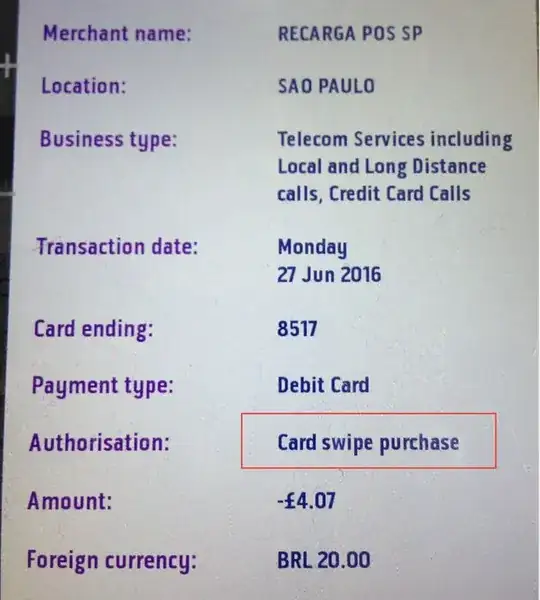
I have a bank account that I never use, someone cloned my debit card and used it to buy something in Brazil in order to make sure the cloning was successful then they started making transactions of £10 till they sucked everything in the account. The account had a little bit over £50, the bank refunded the money straight away as I dont even use the card.
The question is how did they manage to clone my card if I dont use it? Yes it's in my pocket all the time but I never use it to make payment nor I check my balance at the ATM.
The only thing I can think of is that I recently spend a lot of time in the mosque where someone could sit next to me and like in movies use a device to clone my card, is such technology available?