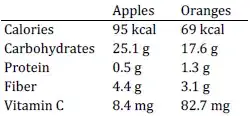
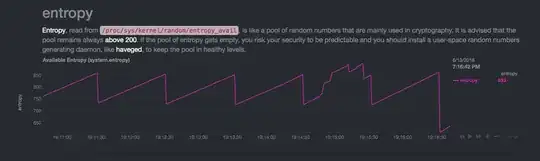
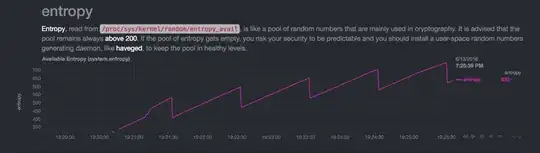
Below are graphs with the value of /proc/sys/kernel/random/entropy_avail on a Raspberry Pi. This answer which might not be correct describes it as:
/proc/sys/kernel/random/entropy_availsimply gives you the number of bits that can currently be read from/dev/random. Attempts to read more than that will block until more entropy becomes available.
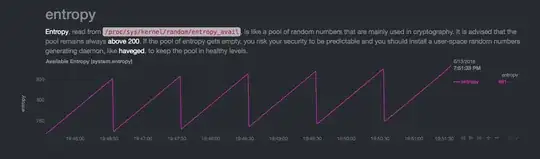
The pattern always comes to the same "stable" saw pattern with ~130 bit decrease every single minute. If entropy grows too much, something is "eating" it to return to the 700-800 range. If I reboot the device, the entropy is still being eaten each minute, but in a smaller chunks thus enabling it to grow again to 700-800 range.
How shall I interpret the graphs? What is happening?
My feeling is that if there was just a process using a random number generator, the entropy_avail once thrown out of balance (by using the device hardware) should either grow infinitely or decrease to the level of 200, when /dev/random would stop supplying the values.
Also if any of the monitoring methods (see checks below) influenced the entropy, it should rather decrease entropy every second, rather than let it grow and drop suddenly at one minute intervals.
(if I leave the machine idle, the stable "saw" pattern continues for days, I took the screenshots in a shorter period of time)
The graphs
The machine is idle for a long time:
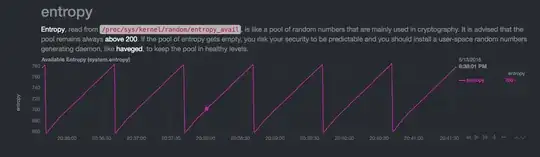
At around 19:14:45 another machine accessed
apt-cacheron the Pi - entropy grew (I guess from network usage). After that at 19:16:30 the drop to "usual levels" was larger than usual (it is also repeatable - ifentropy_availgrows too large, it drops faster):I reboot the machine, the entropy grows until it reaches the "usual" level:
Once again it reaches an idle state:
After another reboot the point in time of the entropy decrease changes, but it still occurs every single minute:
Checks
I stopped
netdata(monitoring program) and checked withwatch -n1 cat /proc/sys/kernel/random/entropy_avail. The value ofentropy_availgrows to ~800 and drops to ~680 at regular one minute intervals.Per advice "trace all processes for access to /dev/random and /dev/urandom" I checked with
inotifywait(idea from an answer to a similar question) on Debian VM and there is no access to either/dev/randomor/dev/urandomat the momententropy_availdrops (of course checking manually logs the event).I used the entropy-watcher to check the entropy as advised against using
watch. The results are still consistent with a steady increase and a sharp drop every single minute:833 (-62) 836 (+3) 838 (+2) 840 (+2) 842 (+2) 844 (+2) 846 (+2) 848 (+2) 850 (+2) 852 (+2) 854 (+2) 856 (+2) 858 (+2) 860 (+2) 862 (+2) 864 (+2) 866 (+2) 868 (+2) 871 (+3) 873 (+2) 811 (-62)
Two questions on Unix StackExchange describing the same phenomenon (found later):