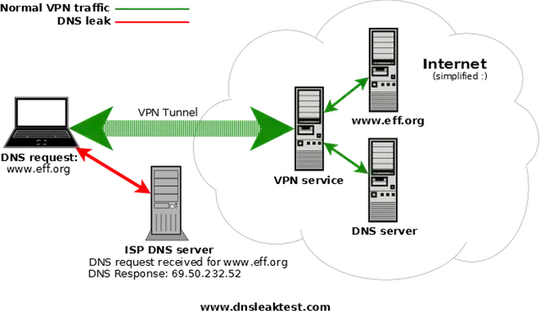
While using your own VPN you can increase your security, putting the DNS server on the side of the network of the VPN service, and forcing any DNS request going through it through your own local DNS service/proxy.
The ISP/DNS provider of the server/network where the DNS is hosted can however log, intercept and modify your DNS queries.
Setting up a DNS server/caching/proxy server that does not talk with the normal root name servers, but instead talks via TLS with dnscrypt enabled servers you solve in one stroke both the privacy element of your DNS requests and any potential leaking.
For additional security, you should setup up also additional firewall rules that intercept DNS requests coming from your premises/your DNS client that are not using your DNS IP address and force the DNS requests to be sent to your DNS service (for instance, a machine with the Google DNS server 8.8.8.8 setup by hand will those be forced to talk with your DNS services instead).
As an additional security measure, please do note that for instance, OS/X and iPhone allow the setup through profiles of VPN on-demand. In other words, any new connection request wont be satisfied without the VNP going up, thus negating any accidental connection while the VPN is not established.
As a side note, at home I run a DNS server that serves my equipment, and use frequently my own Home VPN, the work VPNs managed by me, and a commercial VPN. In this case, there cannot be DNS leaks to the local ISP as I talk with foreign DNS servers over dnscrypt/TLS.
It is also worthwhile to note that whilst services like https://www.dnsleaktest.com test for leak, the "absence" of a leak does not vouch for your setup; those tests are much more useful when they do find leaks.
As a last reminder, I also would add that policies/firewall rules added by a VPN client, especially default rules added by commercial VPN software, may change expected behaviours of your infra-structure.