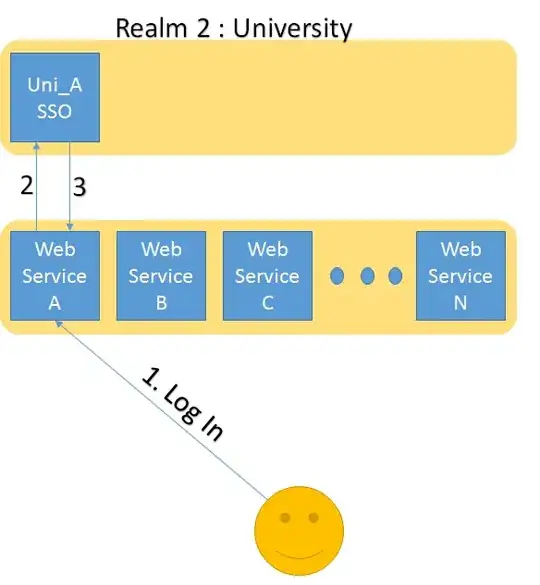
We run a large distributed system consisting of a number (>10) of Django-based web services and web applications with a consumer base of about 10000 university students. Currently, we use a single single-sign-on system (Shibboleth) provided by our university to handle authentication. Authorization/roles are manually configured per-user at each web service. Our current architecture is shown below:
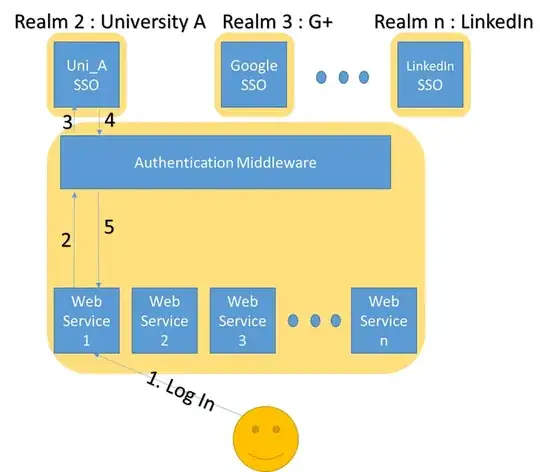
We would like to extend our system to allow logins using Google, Facebook, LinkedIn and other universities. It seems like we need a middleware that is in charge of authentication and role management. Roles are frequently created and cannot be statically defined. The middleware should also perform session management (like handling timeouts, single log-out). We picture something like the following:
What components would we need in this middleware? Our sysadmin is considering Gluu or Keycloak along with an AD service. Would either of these solutions meet our requirements? Are there any best practices or vulnerability/configuration checklists for such systems?