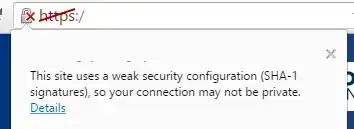
As others have said, technically the risk is small for a MiM attack. However this has a larger problem and implication.
Should I go ahead and enter my card details and pay for something on this site?
NO, YOU SHOULD NOT USE THIS SITE FOR A CARD TRANSACTION
The SSL issue is, as stated by others, relatively minor, however, using a SHA-1 hash means two very important things.
- They have not followed PCI DSS Best Practices. Using SHA-1 in signing certificates, or in the encryption it's self is not recommended, and has to have an exception made for it during an AVS (Automated Vulnerability Scan). Meaning that, last time they did a PCI Scan they had to go out of their way to pass because they were not following a best practice. SHA-1 Hashes can only be used in some circumstances, and only to support legacy setups. You must always support another hash. Because your using windows 10 you support the newer hashes, they are not.
- If they can't bother to do this very simple, easy, and required certification, then they simply don't care enough about the security of your credit card to trust them with it.
Important notes:
- I help clients with PCI compliance all the time. It's fairly straight forward and simple. It takes "some time", but it's a very small investment if your going to handle cards. (maybe 2-3 days with 1-2 hours a day, after a big push of 4 hours on the first day, the first time around, which is mostly reading the rules, for the lowest level of PCI compliance)
- In no way is a PCI Compliance sticker a "I am un-hackable label". It only means that you did a minimum set of things to attempt to protect card data. In may ways it's not even "enough", it's more of a starting point.
- There are different levels of PCI complacence, but the lowest levels (for sites that hand off the transaction to a third party like Paypal to do the actual data collection and processing) sill can not use a SHA-1 SSL cert by it's self.
- All Payment gateways (like PayPal) that I am aware of that let you pass in transaction details (not just a buy now button) require to be the lowest level of PCI compliant.
Note when writing this answer and with comments, significant changes to the answer needed to be made. In short the use of SHA-1 hashes in a PCI compliant setting is very obscure, and relies on a mesh of different rules to allow it. While not currently out right forbidden in current PCI-DSS setups it soon will be. Currently it is allowed only though a combination of clauses meant to support odd/old client(browser) configurations. Most notably the "Older SSL" clauses that allow for insecure SSL setups with other means of security in order to support older (think IE6) browsers. This answer has changed a lot to reflect this. The notes below are from the original answer, but shows, IMO, an important process.
Note After some research this answer, based mostly on the fact that they didn't bother to do the PCI Audit at all, is largely wrong. They could have completed the PCI audit. That being said, the general idea is still true. If they "worked around" the SHA-1 issue instead of just updating to "something else" then my opinion stands. Keep in mind that allowing SHA-1 is supposed to be for "aging, old, and legacy" systems and not as an ongoing practice. You now (today) have to have a migration plan in place even to pass the audit.
More Notes I will have to address this and clean up this answer, but according to "the docs" there is some general rules. First older sites can still offer SHA1 as an encryption or signing option but only if other, stronger options are available too. New sites can not offer SHA-1 at all. Any sites using SHA-1 must have a migration plan. (AVS should auto fail, but you can get an exception). Lastly there is a clear cutoff date for SHA-1 (though it can be moved, yet again)