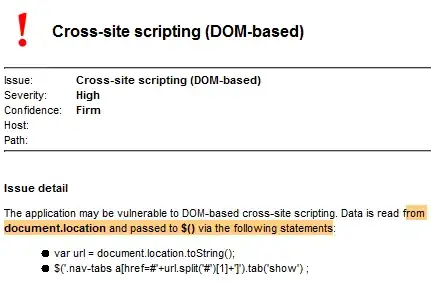
I have come across the following JS code in multiple web applications. I think the reason for the popularity of this code snippet is this accepted answer on SO. Developers seem to be using this code a lot of switching menu tabs:
var url = document.location.toString();
if (url.match('#')) {
$('.nav-tabs a[href="#' + url.split('#')[1] + '"]').tab('show');
}
It basically reads from document.location and passes anything after a # to $() without any sanitation.
Even Burp Suite's Active Scanner reports it as a True Positive.
I've tried to exploit it, but it seems like a false positive to me. My hypothesis is that since JS is converting the URL as a String, any payload (including special chars) will be treated as a string.
Posting this here just to make sure if you guys can think of any other way to exploit it to cause a DOM based XSS?