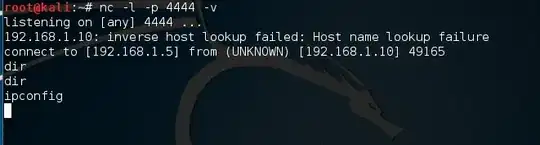
How can I use netcat as a handler for windows/meterpreter/reverse_tcp payload? I am getting a connection but am unable to run any command
Asked
Active
Viewed 2,516 times
1
1 Answers
2
You need to use the meterpreter handler rather than netcat. The issue is that meterpreter uses multiple stages. The reverse_tcp payload is only used to connect back to the client and load the additional shellcode needed to spawn the meterpreter. When you are using netcat this doesn't work.
If you want to have a payload that runs with netcat you need to consider using a regular reverse TCP shellcode rather than meterpreter.
Lucas Kauffman
- 54,169
- 17
- 112
- 196
-
Bro I know that meterpreter is multistaged but I am unable to use metasploit handler. Actually i am getting the error "Connection reset by peer ssl_accept". On investigation, I came to know that I was running my powershell payload using powershell.exe (32 bit method to run powershell payload) which was causing that error. When i tried that payload using %WinDir%\syswow64\windowspowershell\v1.0\powershell.exe , payload run gracefully. Now I have deployed my payload on a victim machine (I cant access that machine). – john May 23 '16 at 14:58
-
Actually I had customized my payload and removed 64 bit method which comes with standard .bat file generated by veil-evasion. Can I get connection using netcat or any other technique? – john May 23 '16 at 14:59