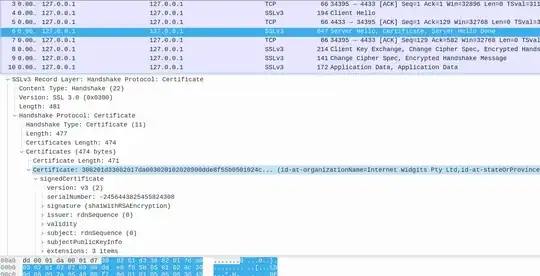
I have a pcap file of 14 sniffed SSL packets. I uploaded it here:
I opened it with wireshark. I see the 14 packets. The largest of seems to contain a self signed certificate (as it is made in a populat internet tutorial). I see the packet contains test like "Some-state" and "Intenet Widgets Pty Ltd" ... How can I actually extract the real certificate (maybe in crt format?