Without even thinking about it, I typed my password into the Google search bar, but I didn't press enter. Since autocomplete is on, does that mean my password has been logged or indexed somewhere? Would it be a good idea to change my password or is that just being paranoid?
-
9Change it just in case. Autocomplete most likely goes over HTTPS but the search engine definitely saved it since they rely on past autocomplete entries to improve it. – André Borie Apr 28 '16 at 23:16
-
22What search bar? Are we talking google.com, a browser url bar, a browser search engine bar, Android homescreen bar...? – Xiong Chiamiov Apr 28 '16 at 23:18
-
8Google Search has Google Instant, so your query is submitted even before you press enter. – Lie Ryan Apr 28 '16 at 23:55
-
1Your password shouldn't be something that autocomplete will complete (dictionary crackable), but change it any time it's been potentially exposed – Fiasco Labs Apr 29 '16 at 05:56
-
1I immediately changed when it happened to me. Related : [Google read your emails](https://www.theguardian.com/technology/2013/aug/14/google-gmail-users-privacy-email-lawsuit). If your password was "LacyLingerie", don't be surprised to see it in your targeted ads. – kaay Apr 29 '16 at 13:19
-
22The answer to any "should I change my password if..." question is "yes, but you probably won't." – djechlin Apr 29 '16 at 20:58
-
1@FiascoLabs The Google autocomplete sometimes adds stuff you type to its dictionary, provided it's not a password field. – reirab Apr 29 '16 at 20:58
-
1Is there some reason that you think any sequence of characters typed into a search box would be interpreted as a password/passphrase by anything? Could happen, I suppose. – user2338816 Apr 29 '16 at 22:40
-
Writing down your password on any medium readable by at least another person, is a security risk. How high? That is another question. – Vladislavs Dovgalecs Apr 30 '16 at 07:26
-
2Your input of 123456 into the search bar *might* trigger that somebody else typing 123 into the search bar is suggested to autocomplete this into 123456. That person might think "Hey, that's a funny character sequence. I guess I'll include it in my dictionary for the next verion of my password hacking tool", and - boom - shortly after many hacking tools attempt to hack accounts by trying 123456 as password. I recommend you don't use 1234656 as password any longer. – Hagen von Eitzen May 01 '16 at 15:57
-
1You're using a password manager, right? Changing your password should take maybe 30 seconds, and you don't have to remember anything new. You should immediately change your password at the slightest hint of anything being compromised. – GrandOpener May 01 '16 at 22:12
-
All your password are belong to us :-) – Bob Jarvis - Слава Україні May 02 '16 at 11:58
-
Don't you think Google already have all of our information? Just my thought..! – Java_User May 02 '16 at 14:28
9 Answers
I highly doubt it.
- You didn't press enter but Google will sometimes send the information to quickly present your results. This is forced over HTTPS. Your information was likely encrypted and not exposed.
- According to most sources Google processes on average 3.5 billion searches per day. There is no additional information to prove your query is a password. Nor is there any public way for a person to get the search queries of a particular Google user. So they would have to be an actual employee of Google. The likelihood of a internal Google employee to trying your search queries as passwords to your account is highly unlikely. It might not even be possible for most standard Google employees to get such identifying information. But if so, the possibility of one with such access purposely targeting you is astronomical.
- Again, there is no additional context to prove it is your password. Nor is your user information submitted with your query. So in the event of a MITM attack where they can read your traffic I would still factor it as real low as they would also have to have your username.
I am going to flat out say there 99.9% chance you have nothing to worry about. If you are wearing a tin foil hat or still have a nervous tick then change your password. If you don't use this password elsewhere then you're golden since it isn't like they could log in with an old password. Otherwise I would move on and not worry about it.
Edit: @reirab made a point it could make it pop up in features that use your search history. I don't believe this happens if you don't press submit. But if you want to be sure clear your search history with Google. I can't be sure this clears it from Google's servers but it should prevent them from popping up in the auto-complete.
- 3,340
- 19
- 26
-
Check our privacy policy. We're very much *not allowed* to look at random user data such as search history. – Kevin Apr 29 '16 at 08:24
-
17@Kevin I'm going to assume baconface wasn't really worried that your internal rules would allow this. Instead it is being written from a worst case, NSA spies on everyone, type of perspective. – DRF Apr 29 '16 at 09:22
-
2is @kevin talking for google? (i see in his profile a hint of employment at big G) – Mindwin Apr 29 '16 at 12:16
-
5
-
7@Kevin you wrote "us". Hard to not take it as speaking for the company. – Mindwin Apr 29 '16 at 13:50
-
3@Mindwin kevin was referring to himself and his alter-egos/imaginary friends ;) – MD-Tech Apr 29 '16 at 13:54
-
19@Mindwin: I don't see the confusion here -- Kevin's comment is not the official statement, but it tells you that an official statement does exist, tells you to read it, and summarizes what you would find if you did. – Ben Voigt Apr 29 '16 at 15:49
-
@Kevin: Do you have any idea how accurately the timing of keystrokes would correlate with the timing of https:// packets? Does each keystroke cause a packet to be sent immediately, or is there some randomness in the timing? – supercat Apr 29 '16 at 16:29
-
1@supercat: Sorry, not on the search team. I imagine you'd run into Nagle's algorithm, but I honestly have no idea. – Kevin Apr 29 '16 at 16:31
-
2I wonder what has higher probability or is more likely: the scenario in the question to where Google or MITM uses the password for a malicious purpose, or a scenario where a remote hacker hacks your machine, installed a keylogger and is actively seeking out account passwords that you type in every day and then uses that password for a malicious purpose. – Dennis Apr 29 '16 at 18:20
-
It's in your search history, G is subpoenaed, it's turned over to the FBI, you're cooked. – djechlin Apr 29 '16 at 20:43
-
@djechlin If Google is subpoenaed for information and they give that information why wouldn't they give them their Gmail or other Google services data on the same silver platter? Doesn't make sense to look for a needle in a haystack when you already have a box of needles. – Bacon Brad Apr 29 '16 at 20:51
-
@djechlin Also read my third bulletin point. To get a password from the results they would not only have to assume it is password with no indication it is a password but know their username as well. – Bacon Brad Apr 29 '16 at 20:54
-
User doesn't necessarily use Gmail. Usernames are not secured. (hint: you can find mine for security.SE at least three times on this page). You don't need to know something is a password, just guess everything. There are 5*10^33 ASCII 16 character passwords but only a few thousand search queries, may as brute force off those first. – djechlin Apr 29 '16 at 20:56
-
5Note that the concern is not just Google employees or the government. Just as I mentioned on another question we had recently from a guy who thought his mother was being able to remotely see his search queries, Google *saves your search queries to your Google account*. Anyone who gets access to any computer (or other device) on which your Google account happens to be logged in and types the first letter or two of your password into a Google search box **will see your password as a search suggestion**. – reirab Apr 29 '16 at 21:06
-
2@djechlin You're right. I was wrong to assume the OP was a normal member of society that had no reason for the FBI to subpoena his search results. Common man, you're nit picking. This is like saying a password that takes 1 million years to brute force is a bad password because it can be done... in a million years. – Bacon Brad Apr 29 '16 at 21:10
-
@reirab Note that the search isn't saved if, like the OP, the user doesn't press enter. – Blackhole Apr 29 '16 at 22:01
-
Searching queries for possible passwords and hoping for the unlikely scenario that someone accidentally enters their password there, is only (marginally) plausible if the targeted person is a VIP, and therefore a large number of manpower and resources are dedicated to spy on that one person. But in that case there are plenty of more optimal attack vectors available. – vsz Apr 30 '16 at 16:47
-
As a minor point. Usernames are far less protected than passwords. I don't disagree with the major point of the answer but I think relying on any level that "They need to know your username" isn't really safe. I don't think it's unreasonable to assume your username is already out there. >So in the event of a MITM attack where they can read your traffic I would still factor it as real low as they would also have to have your username. – Wolfkin Apr 30 '16 at 20:46
-
I have to strongly disagree with this answer. It does not take into account OP's threat model at all, and indeed does not even acknowledge that it exists. Is it his encryption key? Is it a password to a bank? A forum? Does he have to worry about the FBI subpoenaing Google, or just a random hacker impersonating him? If his threat model involves a government agency decrypting his hard drive, then it is horrible advice to say "don't change your password". If your threat model is simpler and it's just the password to a forum, then this answer is much more fitting. – forest May 01 '16 at 00:00
I recommend that you change your password. The fact is, that your password has been sent to their servers, even if you didn't press enter.
You can test that on your own, open your browser, Ctrl + Shift + I, select network, start typing and monitor traffic.
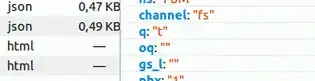
Here is an example, writing the keyword "test", and not pressing enter.
Pay attention to the letter q, which stand for search query: t, te, tes, test, as you can see this is almost the same thing as a keylogger.
- 10,005
- 8
- 33
- 53
-
Pressing Ctrl+Shift+I didn't give me the same view as you. I tried Chrome, Firefox, and IE. What browser were you using? And if it was Chrome, what do I click on after `Network` to get the same view as you? Thanks. – kmort Apr 29 '16 at 13:28
-
1@kmort Using Chrome, press Ctrl + Shift + I, go to the Network tab. Make sure the developer console is docked to the right. Make sure traffic is being recorded (optionally clear the log), and type. You should see links populate like `https://www.google.ca/complete/search?...` Click the link, go to the *Headers* tab, and scroll down to *Query String Parameters*. If you collapse all the other sections it will be similar to what the picture in the post shows. – JSBob Apr 29 '16 at 13:56
-
@JSBob Wow. That is really cool. The step I was missing is clicking on the right URL. Thank you JSBob. – kmort Apr 29 '16 at 14:04
It has been sent (encrypted) to Google. Change your password
It has probably been logged somewhere, along with many search terms and other junk people have typed there. While it's unlikely it will be used for anything you care or that endangers your account, why bear the risk? Simply changing it will solve it.
PS: I recommend using a browser search bar, with suggestions disabled.
- 17,578
- 3
- 25
- 60
-
I don't use one bar for everything, but an address bar, which only have history suggestions and will never send anything to any search engine, and a smaller search bar, which shows suggestions from remote servers. – Gustavo Rodrigues Apr 29 '16 at 11:59
-
@GustavoRodrigues That's also how I prefer it to behave. One can get partway there by using `http://%s` as the default search engine. – kasperd Apr 29 '16 at 16:27
-
12Really your information is most secure if you just don't connect to the Internet. – djechlin Apr 29 '16 at 20:40
Theoretically, you should change your password, as by typing it into google the password is sent to google.
Google does use https however, and I personally wouldn't be too worried about google having my password as a search, but hey, it's not ideal.
Realistically, I think you should be fine, but if you want complete security, it can't hurt to change your password.
- 344
- 1
- 10
-
2With google, https is removed after it reaches google servers, and is stored in plain text. – Mark Buffalo Apr 29 '16 at 00:19
-
That would essentially require an insider at google, or for google to be hacked, right? – Stoud Apr 29 '16 at 00:31
-
8Or a simple request for a users search history by some government entity ? – Chris Apr 29 '16 at 09:26
-
3@MarkBuffalo That's not just Google. Every https server has to decrypt the data it receives in order to be able to process it. – kasperd Apr 29 '16 at 10:55
-
Yes, of course... but they are apparently transferred across several different servers, and there is apparently a *thing* going on with MITM. Google will also sell your search results. – Mark Buffalo Apr 29 '16 at 10:59
-
@kasperd: but not all services *store* user data in plain text, as Mark claims Google does. Almost all, but not all ;-) – Steve Jessop Apr 30 '16 at 21:58
-
@MarkBuffalo That's undocumented speculation, which I see no reason to believe in. – kasperd Apr 30 '16 at 22:01
-
@SteveJessop Most online services will store your data in plain text. The only exception is the login password, which decent services store as a salted hash. For other data you rarely have an alternative to storing it in plain text on the server. – kasperd Apr 30 '16 at 22:03
-
@kasperd [I agree](https://d1udmfvw0p7cd2.cloudfront.net/wp-content/uploads/2013/11/nc20131113d1a.jpg), but if any of those servers are compromised, well, you know. – Mark Buffalo Apr 30 '16 at 22:07
-
@Stoud: well, Google themselves can be considered one big spyware. They use all the data you sent in order to make more money. While they probably will not sell your IP + password to enterprising parties (only because it's bad for PR), they in theory could use it to access your data and use it against you in the war of targeted commercials. – Juha Untinen May 02 '16 at 06:19
It's doubtful, but consider the following
- The connection to Google Search is encrypted. As far as we know, Google Search History has not been compromised. In the event you have Google Search and Web History Enabled, your search history could theoretically be accessed by someone who managed to break into your account. You stated that you didn't press enter; it probably was never stored in your account if that's the case.
- In the event Google logs search suggestions before you hit enter it could theoretically be linked to your IP address and/or account if you were logged in at the time. If your account was court-ordered for information in a timely manner it might be possible for them to retrieve the information and test it against various accounts and/or to use against full disk-encryption. If this is a concern to you then I would change the password in question.
- If someone is actively attacking your wireless connection, has a false root SSL certificate installed on your computer, or using another MITM technique they might guess that it's a password and use it to aid further attacks.
In the end it depends on two factors: who your adversary is and how valuable the password is. If I were in your given situation I would probably just change my password to stay on the safe side.
- 877
- 5
- 10
- 61
- 1
-
1Voted up because the "In the end it depends on two factors: who your adversary is and how valuable the password is." is key. The currently popular answers are simplistic, as they don't include that point. Adding it to the popular answer. – WHO's NoToOldRx4CovidIsMurder Apr 30 '16 at 18:13
Even though it was probably encrypted as others have stated, there's a risk that it may be displayed again as a suggested search if you were to type the same first few characters as part of a real Google search. If it was displayed again it may be at risk from shoulder surfers.
So I suggest you change your password.
- 2,017
- 19
- 27
I think you're asking the wrong question, and will suggest some edits.
Your question ("Because of autocomplete, is my password at risk?") implies you have a single password, and worries about the exposure threat from typing it into a search engine. You probably don't need to worry about that, but you do need to worry that one or more of the sites at which you've entered it has been breached.
These data leaks are common. They impact sites that simply store the password in plaintext (RockU springs to mind) to sites like Ashley Madison, which used a decent algorithm for storage, poorly implemented.
As such, if you have a single password you're using across many sites, it has probably been leaked in association with your email address.
I recommend using a password manager. I think 1Password is a good choice. I use inter-device sync to back up my vault, and I don't store even the encrypted passwords in the cloud.
- 2,659
- 1
- 10
- 12
Theoretically, yes, since your password has been sent to Google and is most likely stored somewhere along with billions of other short strings.
In practice though, the probability of that password getting out of that database and somehow making its way to an attacker that tries to use it to access your account is several orders of magnitude lower than many other mundane attacks you're constantly exposed to. So unless you're running a super high security system (something like a root DNS server or a root CA certificate), worrying about it would be irrational.
In fact, I'd say there's a good chance that the probability of something going goes wrong while changing your password and you ending up locked out or compromised anyway may be higher than the probability of you getting compromised from that.
- 11
- 1
It can't be possible (as far as I know PHP and MySQL). That's because PHP (a language in web development) tells MySQL (database server) to store your input after it's SUBMITTED.
And the auto-completion, I don't know much on it or what language is used to make that kind of feature, but I think it just gets what matches more with your string (i.e your password).
As there's actually no database of Google to store accidental passwords that haven't been submitted.
And even IF they (Google) get the password, they can't tell for which account, for what username. So, stop worrying.
- 123,438
- 55
- 284
- 319
- 171
- 1
- 2
- 8
-
3how then do you respond to all the answers saying that everything you type in the search bar is sent to Google (re: autocomplete, auto-suggestions) – schroeder Apr 29 '16 at 18:33
-
I hope I'm not misunderstanding your question but I'm just gonna pretend that I understood it. Actually, they aren't really "sent", b/c when you say sent, it means that it's submitted and also processed(stored or used as a keyword). So that auto-suggest thing is PROBABLY JQuery or AJAX I'm not sure. Please clarify your question if I'm not understanding it. – Slim Shady Apr 29 '16 at 18:51
-
2How can the search bar return auto-suggestions without "sending" and "processing" on the server-side? Does it really matter what technologies are used? – schroeder Apr 29 '16 at 19:00
-
The codes which I wrote in JQuery consisted of the words that will be shown as suggestions so the suggestions can't go beyond those words. I created a very simple autosuggestion function which was working without processing (it's the nature of the language to be executed anytime like CSS eg. when you hover on a thing in a page it might change colors or have animation yet the page isn't loading again in order to process the hovering). So, what I think is that Google don't store every combination of words to suggest, but rather use either pre-made searches or website contents or both but can't s – Slim Shady Apr 29 '16 at 19:29
-
@BenJunior if that was true, where do you think these "pre-made searches" list would come from? – Rafael Almeida Apr 29 '16 at 19:34
-
-
-
1@BenJunior regarding what is meant by "sent", the hole is much deeper, but even if it was as simple as "the autosuggest thing is AJAX", even then the server has knowledge of what was written in the search box, and from there on, since they know the data, there's nothing you can affirm anymore. – Rafael Almeida Apr 29 '16 at 19:42
-
Okay wait I'm kinda confused right now, not about the password thing but about which side are you in. I mean are you saying like "Yes, it's a big threat" or "Just relax and go watch spongbob like nothing happened" and you're just against me? – Slim Shady Apr 29 '16 at 19:47
-
2No need to deal in absolutes. The fact is - Google servers _do_ get to know your password when you type it even without pressing enter. Google then has the ability to do whatever they want with this data. However, the chance that there will be practical consequences is not big, in this case. Whether you consider this "a big threat", or "a reason to relax" depends on the person's situation - what they have to lose, if they are strict or laid-back regarding security and privacy, etc. – Rafael Almeida Apr 29 '16 at 19:59
-
I'm gonna type in my password, **submit** it and see what happens. Because Google won't know for what (kind of) account and for which username it belongs to. And I'm pretty damn sure nothing will happen except someone is expecting you to unreasonably input passwords in your search box without any other information about the account and already prepared a phishing attack and the page that you typed on wasn't the original Google page rather the phishing page you somehow got into and even more, for these exception you gotta submit. – Slim Shady Apr 30 '16 at 04:25
-
1@BenJunior you are missing the point of the problem with your answer. You state that "it can't be possible". Considering that the question is "has it been logged?" you are stating that the password has not been set to Google because the OP did not hit enter. I think we have shown that to be categorically false. You are now arguing, "it just doesn't matter if it's logged", which is a completely different answer. So, your answer, and arguments, are disconnected, and a little non-sensical. – schroeder Apr 30 '16 at 04:57
-