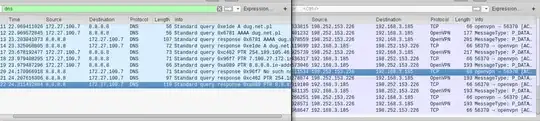
I'm reading about DNS leak and what threat it can pose to VPN users, for instance, this question. But generally, there's tons of similar topics on the internet. But what are people afraid of? I just made a simple test. I started two instances of wireshak. One of them was set to look at the physical eth0 interface, and the other at the virtual tun0 interface. It looks like this:
On the left, you have the tun0 interface with dns filter. On the right it's the eth0 interface. The /etc/resolv.conf file points to 8.8.8.8, so this is the google DNS server. On the left side, you can see some DNS queries, you can see the domain and that the query was sent to google. On the right you see only the encrypted traffic.
So why are people so afraid of? The only thing that google (or anyone) sees is the VPN's IP address. If the VPN doesn't store logs, you can't simply connect a person which uses the VPN service. On the other hand, if the VPN service logs the users activity, then it doesn't matter whether you use their DNS.
Is that true or not?