Row hammer seems to affect ECC memory less, but ECC is still not immune. I have heard of software mitigations like ANVIL, but that doesn't seem to be 100% row-hammer-proof either.
What software or hardware can reliably protect me against row-hammer attacks?
I have found one hint, that certain types of DDR4 memory have built-in protections that work reliably against bit flips and should thus protect against row hammer. But I'm not entirely sure I fully understand it, nor how reliable this protection should be. Would this be a reliable form of protection? A quotation:
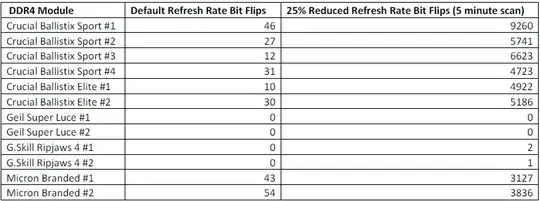
In addition to purchasing a fast Intel Skylake based system, we also acquired four Crucial Ballistix Sport 2400 MHz, two Crucial Ballistix Elite 2666 MHZ, two Geil Super Luce 2400 MHz, two G.Skill Ripjaws 4 3200 MHz, and two Micron branded 2133 MHz DDR4 memory modules for testing… Of the twelve memory modules we tested, eight showed bit flips during our 4-hour experiment. And of these eight failures, every memory module that failed at default settings was on DDR4 silicon manufactured by Micron. The Geil branded modules contained SK Hynix and the G.Skill modules contained Samsung silicon.
Edit: in the other question, it is mentioned that Micron has built in special protections in its DDR4 chips. But I believe Samsung and SK Hynix have done that as well, and, apparently (see above), Micron's protections weren't enough.