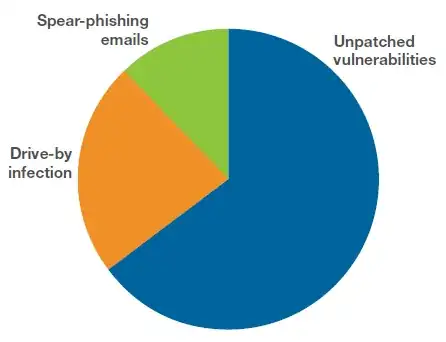
Are you safe from ransomware just by not downloading suspicious files?
Unfortunately, it is a mistake to assume that you are safe from ransomware just by not downloading files from suspicious websites.
As an example, just last month, the OS X version of the popular BitTorrent client Transmission (v2.90) was infected with ransomware. This infected version of Transmission was distributed through Transmission’s official website (their main server was compromised) for a day or two, so anyone who downloaded it then would have been infected. Surprisingly enough, attepting to update within the app (Transmission uses the Sparkle framework) would have been safe, since the attackers apparently didn’t update the checksum for Sparkle in the compromised version, causing the (potentially automatic) in-app update to fail with a signature mismatch.
Unfortunately, I was almost caught by this ransomware. Due to a vulnerability in the Sparkle framework that was recently disclosed at the time, I was manually updating all my applications that used the Sparkle framework instead of updating them in-app, and that included updating to Transmission v2.90 by manually downloading it from the official website. I only managed to get away unscathed thanks to downloading it a few days before the server compromise happened. Honestly, I was pretty scared once I found out about the compromise a few days later. I’d say I learned a valuable lesson here, which was that you can never blindly trust an application you’ve downloaded from the Internet, even from developers you trust (unless you vet the source code yourself).
Mitigating the Damage of Ransomware
The issue with ransomware is that it encrypts all of your files. If you have a way to prevent applications from being able to read or write to any arbritrary file on your system (by running all downloaded applications in a sandbox, for example), that should essentially make the ransomware benign. On Windows, you can sandbox applications with Sandboxie. On OS X, you can intercept all read and writes from applications running on your system with Hands Off! (demonstrated here).
Another solution is to use Qubes OS, which is an operating system that essentially lets you sandbox different activities/applications inside different virtual machines in a very elegant way. It also supports using Windows 7 inside one of those virtual machines as well.