I am attempting to ascertain the boundaries of personally identifiable
information.
That is a legal question, and varies by jurisdiction. Perhaps the best known is California:
(a) The term “personally identifiable information” means individually
identifiable information about an individual consumer collected online
by the operator from that individual and maintained by the operator in
an accessible form, including any of the following:
(1) A first and last name.
(2) A home or other physical address, including street name
and name of a city or town.
(3) An e-mail address.
(4) A telephone
number.
(5) A social security number.
(6) Any other identifier that
permits the physical or online contacting of a specific individual.
(7) Information concerning a user that the Web site or online service
collects online from the user and maintains in personally identifiable
form in combination with an identifier described in this subdivision.
Later case law has added zip code to the list.
In the context of PCI-DSS, are there specific requirements in the
storage, transmission, destruction, utilization of such data?
The only overlap between PCI-DSS and PII is the cardholder name. The PCI DSS does not concern itself with PII; it concerns itself with "Account Data", which consists of the following elements:
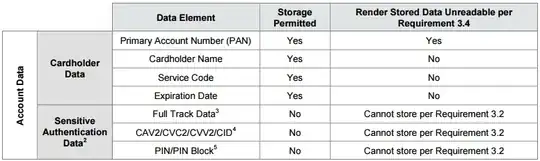
Certain PII elements that may be included in credit card processing, such as billing address and zip code (you may have had to enter your billing zip at a gas station?) are not even mentioned by the PCI DSS. And even for the one clear overlap, the cardholder name, it's fair to say that one's management of the data may be fully PCI compliant but egregiously lacking compliance with applicable PII regulations. You should not consider PCI controls when determining if you are protecting PII correctly.
Following up to comment:
Are there defined controls in protecting PII that also overlap with
PCI-DSS controls?
The problem is that PII laws are punitive rather than prescriptive. They define what PII is and state who is responsible for handling it correctly. They don't define how to handle it correctly; they indicate what sorts of results a correct handler provides and state that failing to provide those results indicates a violation of the law.
The PCI-DSS, on the other hand, is much more prescriptive. It goes into some detail as to the protections expected. It doesn't say what encryption you need to use, but it says you need to use encryption for this and that and correct encryption has to meet reasonable standards.
Could PCI-DSS controls be used to apply to PII data? Sure... you could treat PII as if it was PAN (Primary Account Number) data; make sure it's encrypted whenever stored, etc. etc. However, you'll probably have more trouble because the use cases for PII are different than for PAN; with PAN, you pretty much need to send it to the processor and that's about it. With PII, you may have lots of employees needing to reach in and look at it for one reason or another (customer support? snail mail campaigns? data analytics?) and those people will either be inconvenienced by the encryption, or the protection around the encryption will be weakened by the increased number and variety of access.
There are many criticisms of the PCI-DSS, but perhaps its best defense is, "It's better than nothing." It's a standard, it's imposed by the card brands, and it lays down an acceptable minimum of security controls. There's no equivalent document for PII - all the more so because PII is so jurisdiction-dependent.
