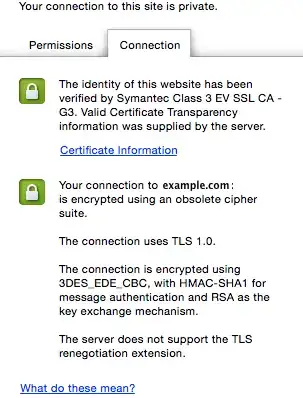
I'm no cryptography expert, but if my understanding is correct, the consequences of what you are seeing are in short, as follows:
Your connection is in fact, encrypted, and as such, should be safer than no encryption at all. Someone sniffing your network, or watching your traffic, should in theory only see encrypted data.
That said, the implementation of encryption that is used for this particular connection is outdated, and could have weaknesses. Why is this happening? I'm not sure. Perhaps because either the server you are connecting to, or your browser, only supports TLS 1.0. This is a little interesting in itself, if the domain name is correct (example.com). When I go to https://example.com myself, I can see it using TLS 1.2 in my browser.
It could in theory be the result of some kind of attack, which forces your browser to use an older encryption standard, so as to be able to exploit vulnerabilities that have been fixed in newer standards, but I would be very careful about jumping to conclusions (assuming you are more or less an average user, and not a particularly interesting target for any reason).
In any case, reverting to TLS 1.0 could in theory open you up to various attacks. So how can you secure yourself against this? The easiest way is probably to simply disable older versions of TLS in your browser.