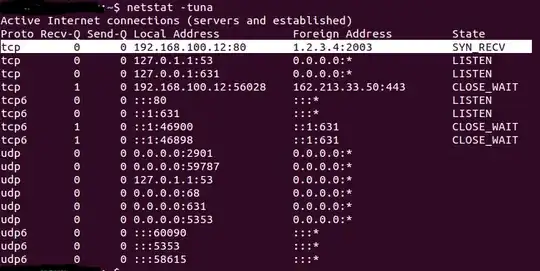
I'm generating a network flood with a lot of packets coming from one fixed IP+port pair (in this example, 1.2.3.4:2003). Why do I only see one SYN_RECV'd packet in netstat on the victim machine?
Asked
Active
Viewed 404 times
2
-
It might be helpful to tell us what kind of packets you are transmitting to your target. It seems like you're only sending SYN packets, so it makes sense on the target you see SYN-RECV,. – Jeroen Mar 27 '16 at 08:14
-
1In addition, TCP spoofing sending multiple SYN request to your target is not going to be very effective. I recommend UDP spoofing as with TCP you can't set up an entire handshake unless you can predict the sequence numbers. – Jeroen Mar 27 '16 at 08:15
-
Syn cookies maybe? – symcbean Sep 14 '18 at 23:27
1 Answers
1
SYN_RECV is a state of a TCP socket which is identified by an IP+port pair. So all your SYN segments fall into the same socket, as the IP+port pair is fixed in your case.
As you probably don't change sequence and acknowledgment numbers as well, the TCP driver on the victim just treats all those SYN segments as retransmitted.
ximaera
- 3,395
- 8
- 23