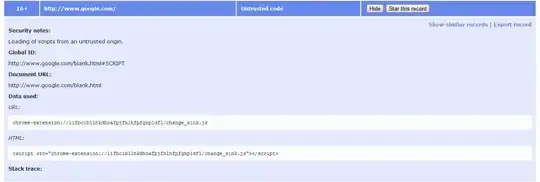
The “untrusted code” is defined by the origin of a resource relative to the current resource via the "safeOrigins configuration". The way DOM Snitch implements this is in my opinion of little value, since if the current resource was modified with a hostile intent, it would not matter if the hostile element was local or non-local.
Information about safeOrigins configuration:
Used by the untrustedCode heuristic, this field specifies the origins
that are considered trusted for hosting scripts, CSS, and Flash
movies.
"safeOrigins" : [".example.com", "foo.example.com/example/"]
Source: Configuration files in DOM Snitch