Eduroam's RADIUS configuration creates a TLS-secured tunnel between your device and your home RADIUS server for the RADIUS Access Challenge.
While the local institution's RADIUS server will see who you are (i.e. your username) (they have to, in order to know whether to authenticate you locally or send you out to the Eduroam network), the actual authentication using the password is done completely inside the tunnel.
Here is a sequence diagram from the documentation:
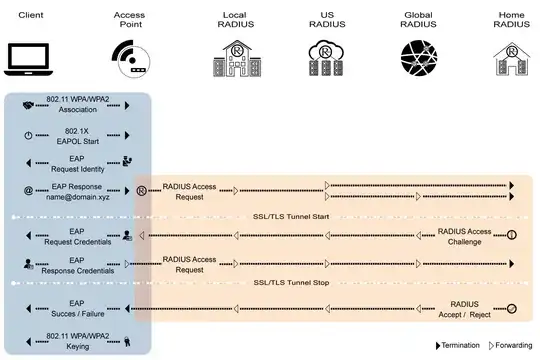
See the Eduroam US Technical Overview for System Administrators for more details.
NOTE: The RADIUS standard does allow you to specify a separate "outer identity" that the local server sees which is different from the one that you actually use for authentication. However, that is typically left unset by default. If you want to anonymize your username, Eduroam allows you to change the outer identity to anonymous@realm where realm is your university's domain.
If you set an outer identity, the local institution's RADIUS server uses the realm portion to determine where to send the request. While the local institution may be able to log the user portion of the outer identity, they do not use it for the authentication. Therefore, it is technically possible for someone else to pretend to be you to the local institution while still authenticating as themselves to their home institution. However, if the two institutions compare their RADIUS server logs, they will easily discover that the other person is pretending to be you. There is no way to hide such things as malicious or criminal activity as long as both institutions are logging access to their servers (which I know that at least some Eduroam institutions are doing).
Additionally, the realm of the outer identity must be the correct one for your institution in order for the authentication to succeed, so there is no way to pretend that you are from a different institution.
For more information about this process, consult the paragraph above Figure 3 and Figure 3 itself on the page linked above.
