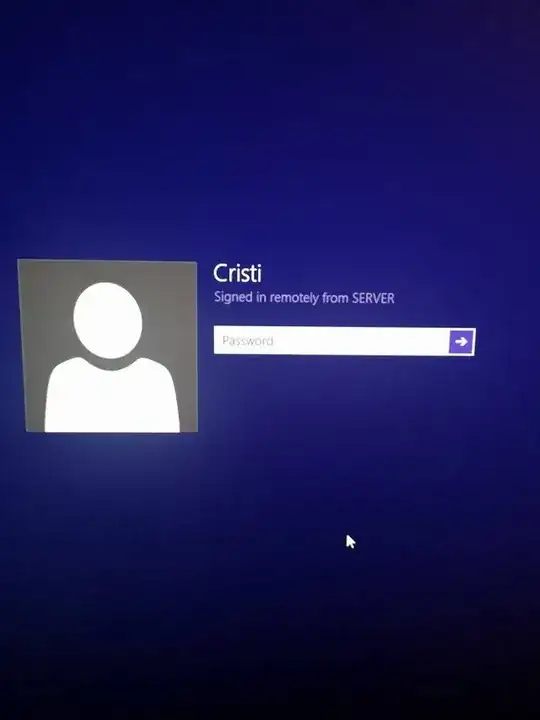
I ve been suspecting someone logging into my computer because a couple of times, during the user log on screen I saw "Signed in remotely from.."
The first timeIi saw some of my pictures copied on the desktop, the second time there were some folders opened when I logged in.
Today, it happened again and this time I was working at the computer. I was logged off out of nowhere, and when I tried to login I saw that someone else was already logged in.
After entering my password, I saw that Web Browser Pass View (which I have not installed on my computer!) was opened and someone tried to save a txt file in the Document folder. I disconnected the LAN cable immediately.
Of course, I changed my windows password a couple of times, but I leanred today that it didn't help.
Has this happened to anybody before? Any suggestions?
I'm running Windows 8.1 Enterprise.