My local network has been exhibiting some inexplicable behaviour.
Firstly connecting to my websites domain name from inside the lan redirected me to my router's login page. I checked again with 3g and found that it didn't happen from outside the network. This has never happened before and has not happened since.
I was worried the page was being spoofed so I didn't submit any data. A traceroute took me straight to my wan ip, with no stop at 192.168.1.1.
EDIT: I believe I have resolved this aspect. I have a dynamic IP address so if it changes (due to power outage or such), I think it takes time for my DynDNS service to be updated. Though this is handled by the router and why it doesn't do this on boot I don't know. Might have to make my own updater.
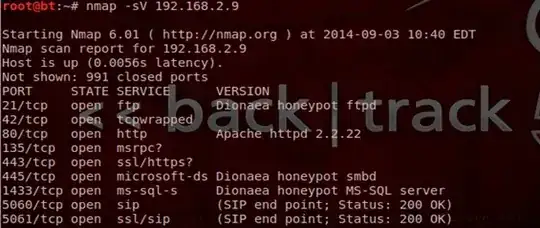
Further, and Nmap scan of 0.0.0.0 revealed this:
$ nmap 0.0.0.0\
\
Starting Nmap 6.47 ( http://nmap.org ) at 2016-02-03 18:14 GMT\
Nmap scan report for 0.0.0.0\
Host is up (0.00075s latency).\
Not shown: 970 closed ports\
PORT STATE SERVICE\
22/tcp open ssh\
80/tcp open http\
83/tcp filtered mit-ml-dev\
88/tcp open kerberos-sec\
139/tcp open netbios-ssn\
280/tcp filtered http-mgmt\
445/tcp open microsoft-ds\
631/tcp open ipp\
1045/tcp filtered fpitp\
1072/tcp filtered cardax\
1081/tcp filtered pvuniwien\
1175/tcp filtered dossier\
1187/tcp filtered alias\
1594/tcp filtered sixtrak\
1658/tcp filtered sixnetudr\
1755/tcp filtered wms\
2222/tcp filtered EtherNet/IP-1\
2381/tcp filtered compaq-https\
2393/tcp filtered ms-olap1\
3527/tcp filtered beserver-msg-q\
3737/tcp filtered xpanel\
4003/tcp filtered pxc-splr-ft\
5102/tcp filtered admeng\
5678/tcp filtered rrac\
5900/tcp open vnc\
6025/tcp filtered x11\
6646/tcp filtered unknown\
9001/tcp filtered tor-orport\
9666/tcp filtered unknown\
55600/tcp filtered unknown\
\
Nmap done: 1 IP address (1 host up) scanned in 6.46 seconds\
I repeated a scan for each machine on the lan and found nothing, netcat was no more forthcoming. I could not find these ports anywhere. Since then the same Nmap scan returns has stopped throwing out these results.
I am worried there may be something nefarious going on...could anyone offer an alternative explaination of this behaviour? I'm not well versed on Nmap.