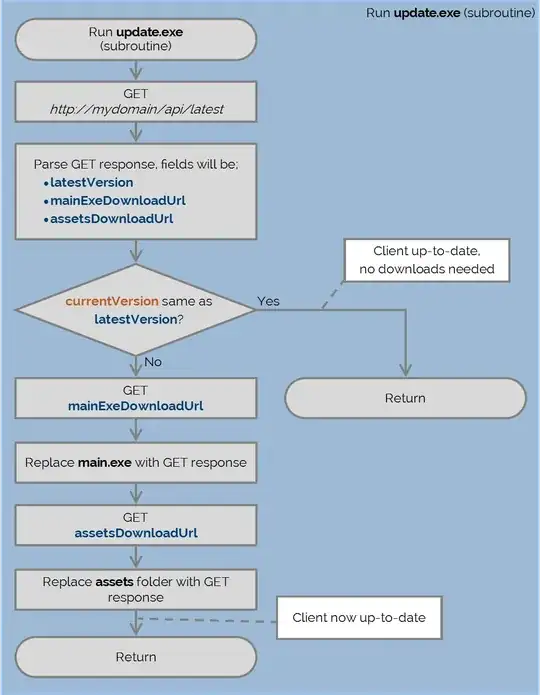
You have essentially two issues in your process: providing the update and having it installed.
Server Auth
Firstly, yes you need to authenticate the server. This means that communication to the server must be done on a secure encrypted channel. Make sure to take the time to understand attacks on SSL so you don't use something that's expired. Ship the certificate with your app, and encrypt all the exchanges. Ship an extra public key for verifying signatures, different from the one used to secure the channel.
Update distribution architecture
Secondly, you must ensure that clients can trust what is being served to them. Assuming the worst, your server could indeed be compromised. You can take two steps to mitigate this. Firstly, ensure that the server used for updates is dedicated. Don't go running that API of yours on a Web server that hosts your personal blog. Run only the update API and think carefully about how you maintain this server and connect to it. Keep it updated. Have a penetration tester break it for you.
Secondly, (thanks @Steffen-Ullrich for reminding me of this) ensure that the server only distributes content that you have validated. When you publish a software release, you should sign your release tarball / binary with a private key (the one for which you shipped the public key) and release the signature along with the tarball. So your process involves uploading signature and binary to the update server and then clients retrieving it from the server. If your server is compromised, clients will no longer receive updates but at least they will not receive bogus / malicious executables.
Replacing the binary on the OS
Surprise surprise. This is 2016, you don't just replace executables system-wide on an OS without permission from the user. You'll have to drive your users through a UAC permission dialog every time you want to change the binary. This is of course going to be annoying for them.
If you expect your clients to absolutely need the latest update every time it's released (and assuming you can't get your app to install with a Integrity Level like browser vendors do), it might be more transparent and pleasant for your users to update your app via Microsoft's app store (saying 'might' as I've never shipped an app there and am unsure about that point).