We've received a random email, which was of-course by the way it looks might be a marketing attempt - however, one always needs for a verification to be done. The email read the following:
We have identified that the website http://example.com/ is serving up malicious content. Attached is our initial report. Please can you confirm receipt of this email by directly replying to the sender.
When we find compromised websites, if we feel it is in the public interest, we inform search engine providers, Law Enforcement Agencies and our customers of the compromise to enable them to make appropriate steps. In some cases, we publish our findings within a reasonable time to ensure the general public are aware of any risks presented by the compromise.
We may be able to provide further information on the compromise as and when our research identifies it.
You have received this email because we notify sites by emailing to industry recognized email addresses for reporting compromised sites. If you have any questions then please feel free to contact us on the address used to send this email.
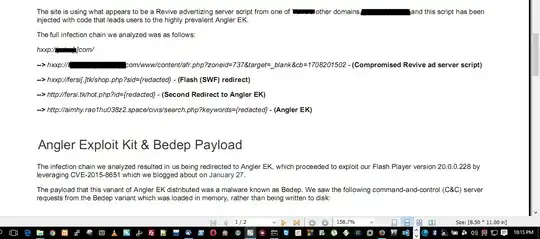
Post this email, we checked up with our Ad-Server for which I came across and inspected the domain which earlier had an open Unvalidated Redirect Vulnerability but was a business use-case and was needed at production system. The URL looks like below:
hxxp://banners.xxx.com/www/content/afr.php?zoneid=737&target=_blank&cb=1708201502
Although a Unvalidated Redirect could be used to redirect users to malicious sites but I am aware our internal servers are not sending any malicious code (we verified this from internal security inspection of all consistent & active code at production Ad-Server). It's hence sending no malicious content from insider organization servers to any external entities.
My question is, why all the Ad-severing servers are termed as CnC in most reports like they claimed in this below report and how do we respond?
Can we otherwise deploy a known tool to detect if there are any certainty on our Ad-Server for the results delivered in end-reports or treat it as a complete marketing agenda since with manual inspection, we looked down to header level & packet level data which shows false positive.