As pointed out by @王庭茂 and @LieRyan, you need some way to prove that the public key that gets uploaded with the license file actually came from your company and wasn't planted there by an attacker (in your case, someone trying to forge a license file without paying). The solution to this is to have your public key made into a certificate.
Looking at your use-case, I don't actually think that a publicly trusted Certificate Authority is what you want. Instead you should set yourself up a private Certificate Authority hierarchy (this can be done in-house for free and with minimal effort with OpenSSL). It's not as scary as it sounds - a CA is really just a public key file that OpenSSL can use to sign other files or certificates.
You should set up a few OpenSSL CAs like this:
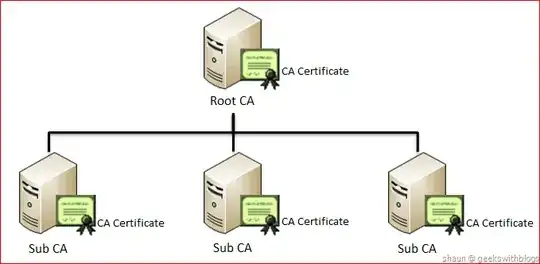 then embed the Root CA certificate in the source code for your application (this is called certificate pinning). The Root CA exists to be an anchor of trust, but doesn't actually do anything other than signing the certificates of sub-CAs. In most cases you can actually take the Root CA offline after you've created your subs. The sub-CAs are the ones that you use day-to-day to sign stuff. Usually the sub-CA would sign signing certificates that you use to sign the license files (creating another layer in the tree), but in your case you can probably get away with having the sub-CAs sign the license files directly if that's the only thing you're using them for. This way you have the flexibility to use multiple keys as you mention in your point #2 (each sub-CA is basically just a signing key), or even to remove a key and replace it with a new one - if you ever need to - without any disruption of service or needing to send out patches.
then embed the Root CA certificate in the source code for your application (this is called certificate pinning). The Root CA exists to be an anchor of trust, but doesn't actually do anything other than signing the certificates of sub-CAs. In most cases you can actually take the Root CA offline after you've created your subs. The sub-CAs are the ones that you use day-to-day to sign stuff. Usually the sub-CA would sign signing certificates that you use to sign the license files (creating another layer in the tree), but in your case you can probably get away with having the sub-CAs sign the license files directly if that's the only thing you're using them for. This way you have the flexibility to use multiple keys as you mention in your point #2 (each sub-CA is basically just a signing key), or even to remove a key and replace it with a new one - if you ever need to - without any disruption of service or needing to send out patches.
To actually implement this, you'll have a sub-CA sign the licence file, and then send the licence file and the certificate of that sub-CA together to the customer. You'll need to link OpenSSL into your application so that it has the logic to validate a certificate. When you upload a license file to the application, it will validate that 1) the license file is unmodified (aka check the signature), 2) that the signature matches the key in the sub-CA cert, and 3) that the signature on the sub-CA cert matches the root-CA cert that's embedded in the application's source code. You now have a proper, secure, Public-Key Infrastructure without any need for the application that's accepting the license file to have internet connectivity!
I'll also address the preemptive question "Is it really worth all the hassle?". The answer is: I don't know, that's up to you. How much do you charge for a license? $5? Probably nobody's gonna bother to crack your license format. $500? You can bet people will start publishing fake keys online. From your question, you've obviously decided that it's worth going down the public-key route. My opinion is that with security you should either do it properly, or not at all. Providing something that looks like security, but is easily broken, won't prevent even mildly skilled attackers, and will give your customers a false sense of protection (maybe leading to outrage when they find out).
