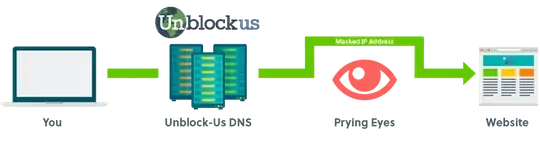
Looking at a Unblock-US Features (a DNS provider) on their website it states the following:
Stay out of the radar of prying eyes.
With Unblock-us, you’ll have peace of mind knowing that your ISP or government is unable to view your online activity. We only send a small percentage of data to the websites we support through our secure servers, and we never log or analyze any data passing through.
The solution to this invasion of privacy? When you sign up for Unblock-Us, you’ll receive a new set of DNS codes to add within your device’s settings. Your true IP address will then be masked and you’ll be able to bypass any restrictions or spying implemented by your ISP or government, all with this simple switch.
So my question is:
How can changing your DNS prevent your ISP or government from seeing your online activity?
If my understanding of how a DNS works is correct I don't see how these claims are possible