In using a VPN service I want to feel comfortable in the knowledge that outsiders cant simply build up metadata on my browsing activities. The fact it is done is somewhat unsettling. I have spent days setting up and configuring a VPN connection for the purpose of transmitting only data which is absolutely necessary to navigate the internet. I ran many tools, conducted online tests and followed many tutorials in configuring patches/fixes for known security flaws.
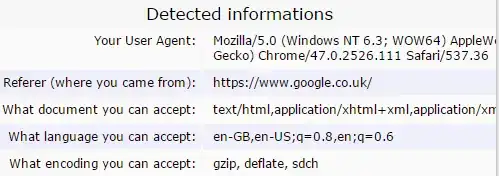
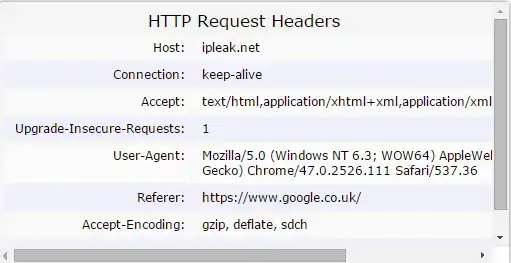
Whilst running VPN service I used https://ipleak.net/ for checking status of the connection and it revealed things were able to be obtained and had to be fixed. The methods I used to fix them all are described at the bottom of the page.
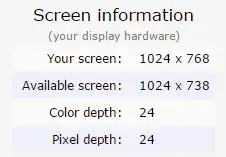
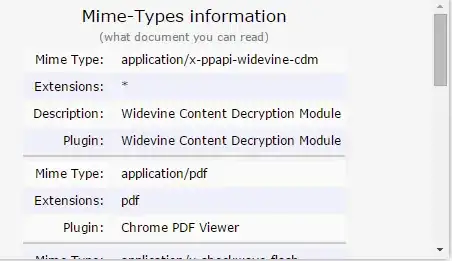
PROBLEM is even when every measure I can find on the internet has been taken the website (https://ipleak.net/) is still able to obtain knowledge about:
My Screen Display (Resolution, Pixels & Colour Depth).
Information on all my installed browser plugins.
Types of documents my system can read.
The Referrer. (Website I Came From)
I would rather transmit as little as possible and feel some of this information obtained is completely irrelevant. I cannot find anything via the internet on any methods which I can take to resolve any of these issues and to stop the information being passed on. Looking for advice and opinions regarding this matter. Appreciated In Advance.
After deciding on using VPN service I conducted the following steps:
- Set up Client VPN Gate Relay.
- Configured IPv4 settings to set Ip address to static. Also changed DNS Servers to 8.8.8.8 and alternate of 8.8.4.4.(Google Servers)
- Disabled IPv6.
- Patched known security flaw known as WebRTC which allows website owners to attain both the VPN Server address as well as your ISP assigned IP.
- Configured and fixed the system so no DNS requests were being leaked. In the leaking of DNS Requests cause a problem as information can be obtained through the fact you are using the ISP Servers to navigate through the internet.(I.E Browser Search)
Here are some Images showing the fact the the website can retrieve all this information while I am using VPN software even after everything I have tried and searched for.