Is it normal for multiple intermediate CA certs to have the same Subject Key Identifier? Why does this happen? I always thought that this was a unique attribute.
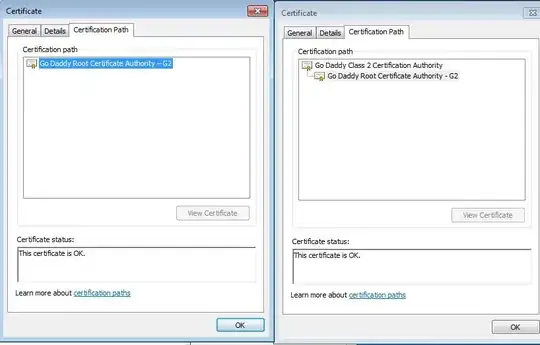
I have come across some odd cases where the intermediate CA that Windows suggests (under the Certification Path section of Crypto Shell Extensions) belongs to a different chain sequence than the one that the certificate authority provided.
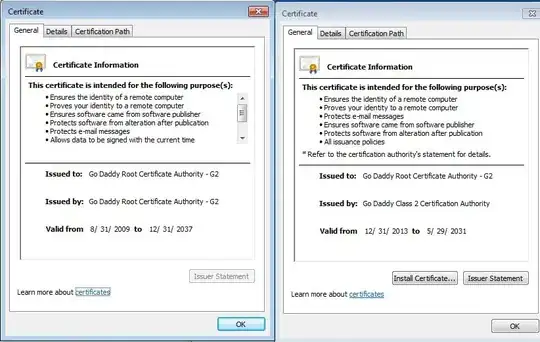
For example, here are two GoDaddy Intermediates. "Issued To:" is the same but "Issued By:" is different:
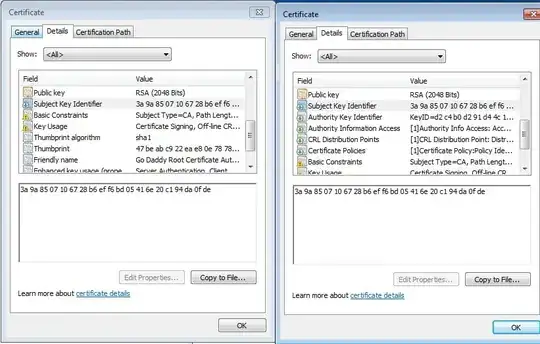
If I check the Subject Key Identifier for both, they're the same:
One seems to be a root but the other is an intermediate:
Windows is pre-loaded with one but the CA (GoDaddy in this case) gave me the other.
So, why do these exist and what is the difference between them? Neither appear to be revoked and I didn't manually add any of these intermediate CA certs to my Windows trustStore.