EDIT (7/7/2016) - see addition at the end of post
I have been keenly following the issues with regards to Microsoft deprecating the use of SHA1 code-signing certificates for Windows executables (http://social.technet.microsoft.com/wiki/contents/articles/32288.windows-enforcement-of-authenticode-code-signing-and-timestamping.aspx).
We are now into 2016, and as we will need to sign and release code shortly, I am trying to verify that, indeed, without upgrading our code signing certificate to a SHA256 one, we will have problems. However, I seem unable to demonstrate any expected problems.
I have signed some executables (today, in 2016) using the SHA1 certificate and configured AppLocker to run only signed executables (I have verified this - I cannot run unsigned executables). However, I am still freely able to run my newly SHA1-signed executables, and additionally, downloading these files from a web server in IE does not present me with any 'warnings' (as I had expected) - the security scan returns that all is good with the files!
I am running the tests on Windows 7.
What actual problems should I expect to experience?
(in case you are wondering why we don't simply just upgrade to SHA256 anyway - there are multiple reasons: one is bureaucratic, but the other is the fact that we also sign VBS scripts which currently do not support dual signing).
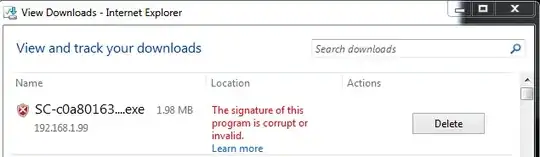
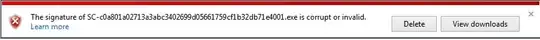
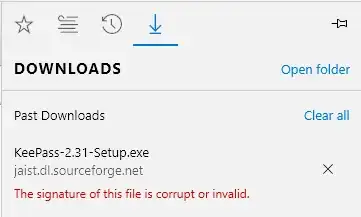
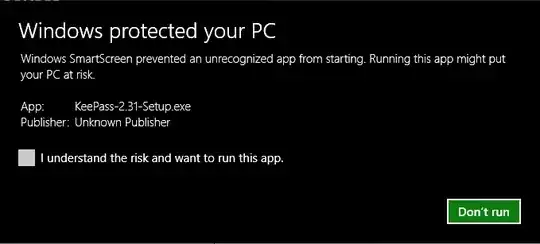
EDIT (7/7/2016) Well, it seems that Microsoft has finally put out an update to IE and Edge that warns you if you download an executable which is signed only with a SHA-1 certificate! Basically, with IE 11.0.30 or later, if you download an executable which was signed with a SHA-1 (but not SHA-256) cert AFTER 1/1/2016, then you will see one of the following warnings:
I guess Microsoft is finally getting in with the warnings in preparation for the 1/1/2017 cut-off. It's important to note that for the moment, apart from these warnings, there are no other changes - the files still execute without problems, and of course, downloading them in other browsers do not cause problems.