Based on information on this page, Windows actually trusts many more root CA certificates than what are displayed when a user launches certmgr.msc and navigates to Trusted Root Certification Authorities > Certificates.
According to the article, the actual trusted root CA certificates are not only those that are shown to the user in certmgr.msc but all those in the Certificate Trust List maintained by Windows on the local machine.
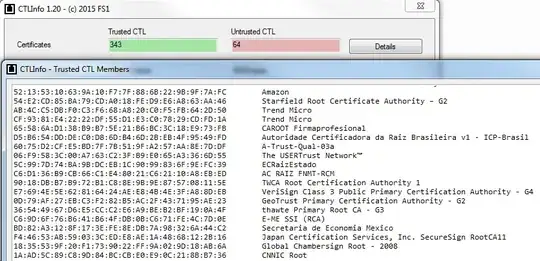
On my Windows 7 machine, the "CTLInfo.exe" tool (provided by the author of that article) listed an output of 343 root CA certificates. This is definitely lot more than the 36 that I currently have in the Trusted Root Certification Authorities store under my user account.
Some of these are shown below.
Looking further into this I then followed below steps (taken from a comment left in above article) to generate an SST (Microsoft serialized certificate store) file with trusted root CA certificates from a Windows Update server:
- launch a Windows command prompt and browse to some folder where you want to generate the SST file.
- execute:
certutil -generateSSTFromWU roots.sst - double-clicking the generated
roots.sstfile should open it incertmgr.msc. Alternatively if the .sst extension is configured to be opened by some other software on your machine, you can execute the following in the same command prompt:start explorer.exe roots.sst
The SST file I obtained through above steps also had 343 root CA certificates, some of which are shown below.
It probably does not matter so much whether one uses the authors tool to look at the certificates, or if one generates them to a separate list using the second method (the latter option provides more flexibility for working with the certificates however).
Update 1: One of the answers says that a large amount of the 300-something missing certificates should be visible under the local machine account.
So I have now used these steps to verify the amount of certificates that are under the Local Computer account on my machine:
- Click Start and type
mmcin the run prompt. This will bring up an emptyMicrosoft Management Console. - Select
Add/Remove Snap-Infrom theFilemenu. - In
Available snap-ins, selectCertificatesand clickAdd. - Select
Computer Account. - Select
Local Computer. - Click
Finish.
Looking at the results, the amount of trusted root CA certificates displayed under the Local Computer is 37. Today this happens to be exactly the same as the amount listed under my User account because it looks like Windows added a trusted root CA certificate since I originally posted this question.
In fact the trusted root CA certs listed under Local Computer seem to be the same as those listed under my User account. But even if they were not, the sum total of these two groups would only be 74; a majority of the 343 certificates is still not visible.
Bottom line is though that a wast majority of the 343 certificates is not displayed through this means either.
End of update 1
Anyway, looking at the 343 root CA certificates trusted by Microsoft, it seems that most of them would not even be applicable for me here in USA.
Or they could possibly be applicable if I needed an encrypted connection to some server in, say, Tunisia or China. On another hand, if I ever do create an encrypted connection to some such server using IE, the browser will probably not complain much because the needed root CA is already in the CTL on my machine.
Update 2: I thought that having all trusted CAs in an SST file separate from the certificates visible under Local Computer or Current User would make it difficult to explicitly ban any of them. For example it seems the at root CA that Google is planning to stop accepting (mentioned here) is still provided by Microsoft in the SST generated by above steps.
However I noticed that merely viewing the root CA certs in the opened SST files adds them immediately to the Trusted Root Certification Authorities group that is visible in certmgr. So after refreshing certmgr, the new root CA can be dragged to the Untrusted Certificates group.
This would have to be done separately for each viewed certificate however.
End of update 2
So the questions I wanted to ask about this are:
- Why doesn't Windows display all 343 root CA certificates if they are potentially willing to use them (depending on my web browsing needs) at a future date?
- Are there any potential security problems from the fact that Windows does not display all trusted root CA certificates through
certmgr.msc?