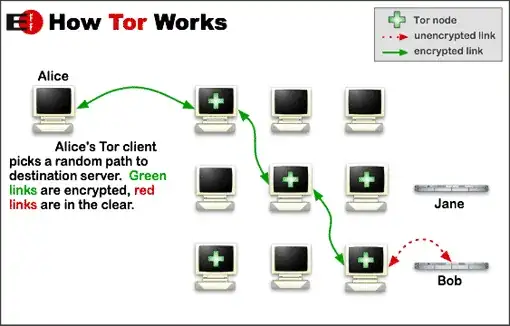
I read on the documentation about the security issues on Tor, that it is ok if the website is running on HTTPS, but how about on Orbot and site that is not running on HTTPS?
Even if it is running on HTTPS is it 100% sure that the end node can not expose data that is sent out?
I am just wondering for the Orbot app maybe even Tor, what if an encryption is added for the data passing back and forth.
For example:
- Encryption for data
- Onion layers are added
- Onion layer removed
- Decryption
It is similar to what the "HTTPS" is doing, but about for Orbot? And if for example a unique private key is used and AES-256 encrypt dynamically for each browser? Even if a server is compromised, or malicious end node, would it make it more secure?