I have recently setup "2-step verification" for my Google account.
One of the features is the ability to create "Application-specific passwords " for devices that do not support the 2 step process. (Apps on smartphones such as Android, BlackBerry or iPhone, Mail clients such as Microsoft Outlook, Chat clients such as Google Talk or AIM)
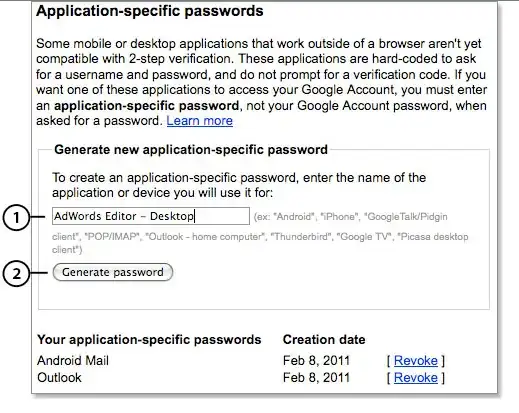
When you create one of these passwords, Google tells you that the "spaces" don't matter.
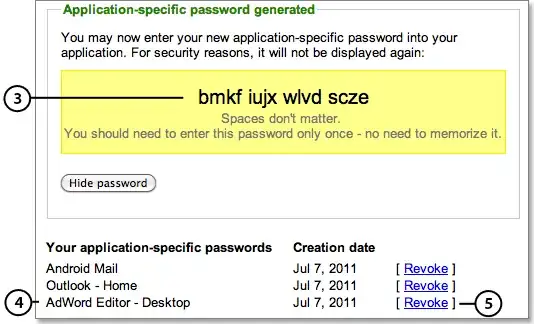
Does this mean that…
- passwords are sent in plaintext, and they can therefore strip out the spaces on the other end (I know mail clients may do this, but would Google products such as Gmail and Calendar or ActiveSync)
- the hashing methods they use strip out the spaces (but they wouldn’t be able to control how 3rd party products hash)
- they store two hashes of the passwords on their end, one with spaces & the other without (If this is the case, wouldn’t they have to store more than two, one for each possible combination of 3 places where a space may be)