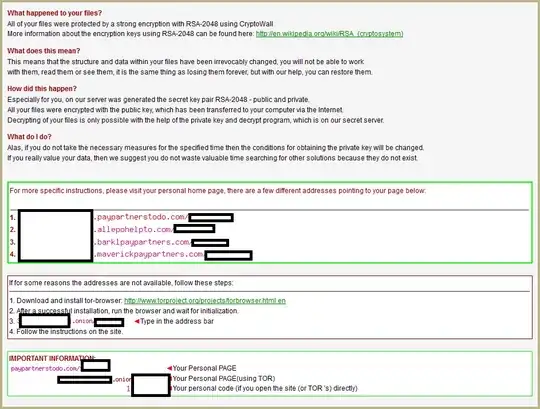
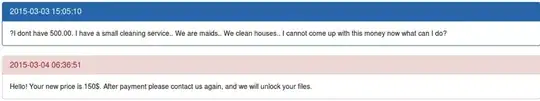
There are some reports of people getting their files back, however
other people have reported being requested a second -unexpected- payment after that (not that surprising, given this is an extortion)
or simply spending the money and not getting their files back
It's even possible that the criminals themselves are not able to decrypt them. Perhaps the user managed to encrypt itself twice, their encryptor is buggy, their "recovery" tool corrupts the encrypted file even further, there may have been a network problem when sending the key to the C&C, their server have been seized... Some ransomware families provide free decryption of a single file to prove that they are able to. Use wisely
Also note that depending on your location, it may be illegal to pay the ransom (you are financing criminals).
I'd prefer paying an AV for recovering the files rather than the criminals. It may even be free if you had their brand installed. See for instance Dr Web's
I also find interesting the claim that the business has decided that paying the ransom is cheaper then rebuilding and trying to recover. Even if you pay the ransom and get your files back (which is dubious at least), you should rebuild the infected structure. How are you going to trust the machine they managed to infect? Plus, they need to take measures so it doesn't happen again. And in this case they don't even know how they infected them!
It's surprising to find out companies that fell victim of cryptolockers... only to be reinfected some months later, and still not having any recovery means.
Just not being able to recover the files from the Shadow Copies means the virus managed to disable them, which leads to the question Why were your users running as an Administrator?
Or not having a (working) backup plan, which may breach national regulations.
You can't simply decide to pay and hide the problems under the rug. If you got hit by a ransomware and you are not able to recover and proceed working in a matter of hours (a few days at most), you have a big problem. As they have found out the bad way.