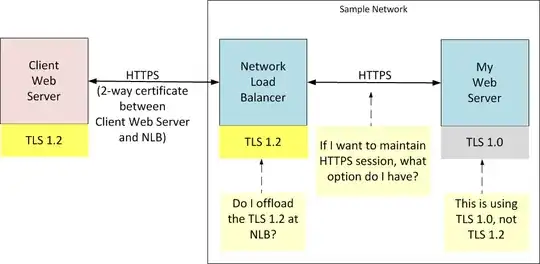
I have a situation that can be better illustrated in the network diagram below.
My scenario:
- Client Web Server (external party) is using TLS 1.2.
- In my network, My Web Server is fronted by a NLB (Network Load Balancer).
- The NLB is using TLS 1.2, supporting 2-way certificate authentication between Client Web Server and NLB over HTTPS connection.
- My Web Server (old server) is using TLS 1.0.
Questions:
1) Is it the best practice / recommendation to terminate (i.e. offload the TLS 1.2 certificate) at the NLB side?
2) If I want to maintain HTTPS connection between the NLB to My Web Server, what options do I have? Note that My Web Server (old server) is using TLS 1.0. Are there any limitations to options?
Any recommendation will be appreciated.
Thanks, Medan