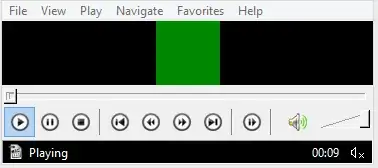
I've downloaded a .wmv file using P2P. Attempting to play it with Media Player Classic (K-Lite Codec Pack) only gave me a green square in the playback window:
I noticed that the video came with a readme file, however; I found the following inside:
This video has been encoded using the latest DivX+ software, if you are having trouble playing this video please try windows media player Media Player should automatically update any out dated codecs
Since the K-Lite Codec Pack is my media software of choice, I decided to visit their site to see if there was an upgrade available. Indeed, the latest version at the moment of writing was released on November 19th 2015 (the version I was using had been installed on my PC at the beginning of November because I'd bought a new hard drive and reinstalled the OS). I've downloaded and installed the update, but nothing changed, I still got the same green square.
Now, this part I am ashamed of; instead of getting suspicious, I did what the file suggested, i.e. ran it in WMP, which indeed suggested that I download some codecs. I let it do it, typed the admin password because my account is a regular one, and then a few interesting things happened.
- UAC has been disabled without me doing anything; Windows showed a prompt telling me that I need to reboot to disable it, and when I checked the settings, it has indeed been turned off
- Opera Browser has been installed and a shortcut was put on my desktop
- NOD32, the AV I'm using, went crazy: two HTTP requests have been blocked and two executables quarantined, logs follow:
Network:
15/11/22 3:35:29 PM http://dl.tiressea.com/download/dwn/kmo422/us/setup_ospd_us.exe Blocked by internal IP blacklist C:\Users\admin\AppData\Local\Temp\beeibedcid.exe desktop\admin 37.59.30.197
15/11/22 3:35:29 PM http://dl.tiressea.com/download/dwn/kmo422/us/setup_ospd_us.exe Blocked by internal IP blacklist C:\Users\admin\AppData\Local\Temp\beeibedcid.exe desktop\admin 37.59.30.197
Local files:
15/11/22 3:35:38 PM Real-time file system protection file C:\Users\admin\AppData\Local\Temp\81448202922\1QVdFL1BTSQ==0.exe a variant of Win32/Adware.ConvertAd.ACN application cleaned by deleting - quarantined desktop\admin Event occurred on a new file created by the application: C:\Users\admin\AppData\Local\Temp\beeibedcid.exe.
15/11/22 3:35:35 PM Real-time file system protection file C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\51L9SWGF\VOPackage1.exe a variant of Win32/Adware.ConvertAd.ACN application cleaned by deleting (after the next restart) - quarantined desktop\admin Event occurred on a new file created by the application: C:\Users\admin\AppData\Local\Temp\beeibedcid.exe.
beeibedcid.exe had been running as a process before I killed it manually using the task manager. Even though ESET didn't touch it, it's no longer in AppData\Local\Temp.
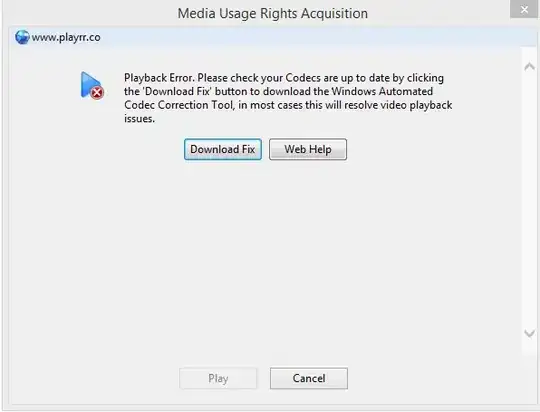
Upon closer inspection, I realized that the prompt WMP opens to allow me to "update my codecs" doesn't look like a WMP component:
The UI differs in certain subtle ways, and the sentence composition/syntax is poor. Undeniably though the most suspicious thing is the domain in the upper left corner, playrr.co; a simple whois lookup reveals that the domain has been registered on November 17th this year - five days ago - and the registrant is WhoisGuard, so the actual registrant clearly wanted to conceal their details.
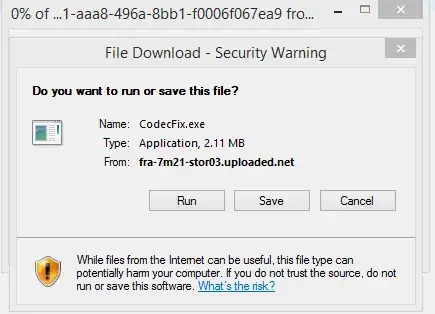
Note that clicking both "Download Fix" and "Web Help" has the same effect; the following IE download prompt pops up:
I should add that the video I downloaded had been uploaded on 2015-11-22 13:29:23 GMT, roughly an hour before I downloaded it. The OS is Windows 8.1 Pro x64 and the AV is ESET Nod32 AV 7.0.302.0, with the latest signatures.
I'm annoyed at myself because this is a fairly obvious trap, but at the same time I'd never think to check Windows Media Player dialogs for obvious trojan/adware!
- How does this thing work? It couldn't have possibly affected my Windows Media Player executable before it was played because it's a media file. Is this a recent vulnerability discovered in the software? Because I doubt Microsoft would allow media files to specify a site to download codecs from...
- No matter what it is, it seems to be a relatively new thing. What can I do to ensure others don't fall for this? I don't think any AV vendor would allow me to submit a
.wmvfile a few hundred megabytes in size for analysis.
Thanks for your time.