A couple of days ago I was having a conversation using Skype, then I wanted to share a link to a page with the interlocutor. I didn't want to let her understand the link content by just looking at the URL so I shortened it with Google shortening service, then I wrote her the link.
The service let me know how many times (telling also the referrer and the browser) the link has been clicked. I noticed immediately that someone located in U.S clicked the link (identifying as Chrome and www.google.co.in as referrer).

(Firefox clicks are mine)
I asked to the interlocutor if she pressed the link (even though we're in Italy she may have some strange network configuration), but she ensured me that she didn't.
Should I suppose that someone is spying my Skype conversations?
Update 1 - Unshared links details
I just noticed that 9 days ago I created a link with the shortener, but then I did not share it with anyone, only me clicked it and this is the result of the Google charts:
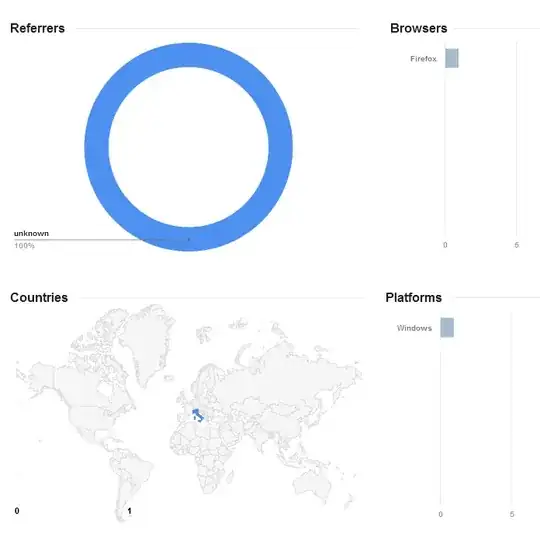
So can I exclude that the link I shared on Skype was visited by Google (if it was, why this link is not visited by no one?), or at least that if Google visits it they don't show their visit in the Details page?
(I have more than one link generated and not shared and no one of them result visited by Google or other except me)
Update 2 - All the shared links are visited by someone who shouldn't!
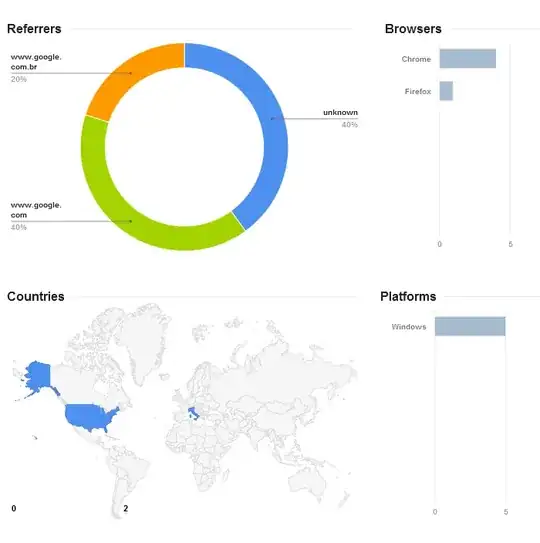
I also noticed that all the links I shared with Skype in the last 2 weeks have been visited at least once by a Chrome browser (with Google referrer), the most particular is this:
Total visits are 5, one is mine (the only Firefox), another one (with Chrome) is the click done by the Skype interlocutor (I'm pretty sure that she visited it just one time because the count of visits from Italy is 2 (my click and her's)).
Who made the remaining visits? If it was Microsoft, why the referrers are www.google.com.br and www.google.com and the browser identifies as Chrome?
Update 3 - About Skype URI preview
@Ankit Sharma said that it is possible that Skype URI preview functionality is looking at the link I shared, so I wrote a simple C# program to check this, here is the code:
var request = (HttpWebRequest)WebRequest.Create(theURL);
request.UserAgent = "Mozilla/5.0 (Windows NT 6.1; WOW64) SkypeUriPreview Preview/0.5"; // This is the UserAgent he wrote in his answer
var response = (HttpWebResponse)request.GetResponse();
using (var sr = new StreamReader(response.GetResponseStream()))
sr.ReadToEnd();
I run this code and then I checked the Details but it didn't record anything.
To check if my program was buggy I tried changing the UserAgent to Opera/9.80 (X11; Linux i686; Ubuntu/14.10) Presto/2.12.388 Version/12.16 (taken here) and rerun it, then I checked at the Stats and it is now showing an Opera click.
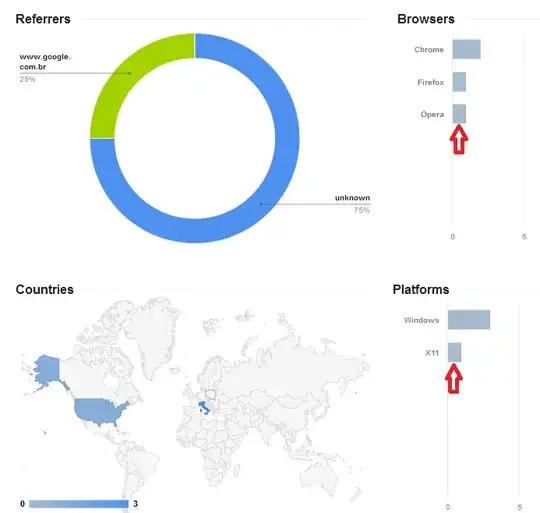
So I think that it is not due to Skype "functionality" that the suspicious clicks appear.