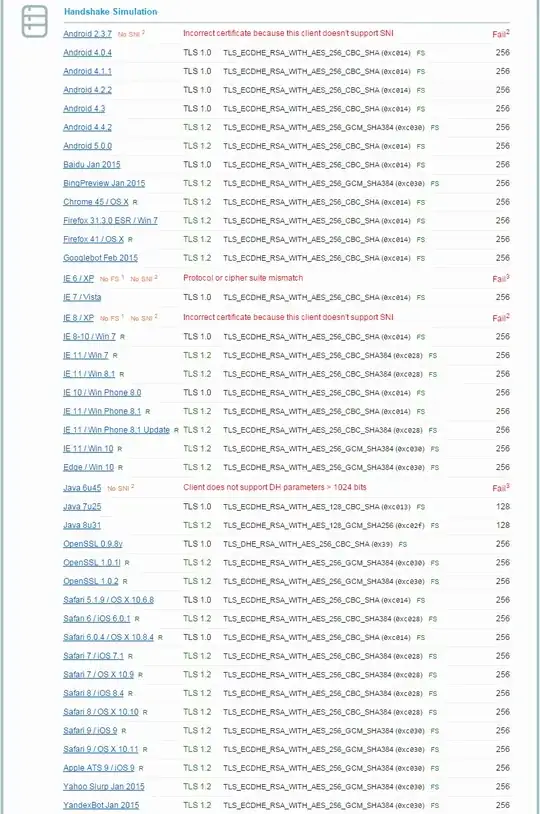
If you disable SSLv3 on your site, then older browsers that do not support TLSv1 or higher will not be able to connect to your site by SSL/TLS.
Having said that, SSLv3 has been deprecated for some time, thanks to POODLE. As a result, many web sites that employ SSL/TLS have stopped supporting SSLv3 for a while now. So, users that are still using older browsers that do not support TLSv1.0 or higher are likely to be having problems connecting to many sites by SSL/TLS (in addition to yours if you've disabled SSLv3).
In fact, in addition to the payment card industry (PCI) requiring sites that accept card information to disable SSLv3 - they are in the process of mandating that these sites phase out support for TLSv1.0 as well. Soon, all sites that accept card information will be required to support TLSv1.1 or higher.
Edit: See this Wikipedia page for a good reference on SSL/TLS protocols supported by various browsers.