imagine I have an architecture as shown.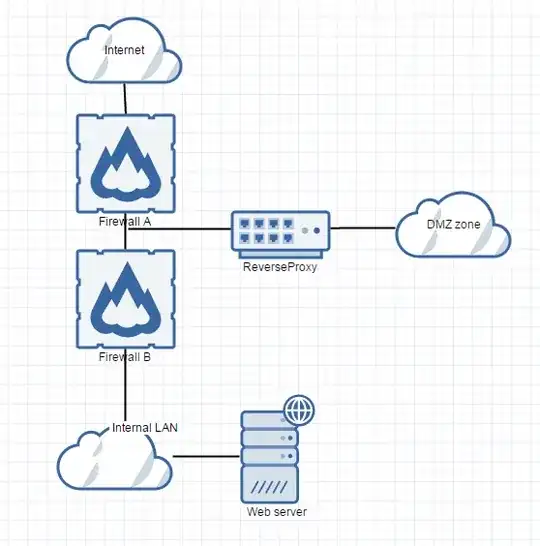
In order to get to the internal web server, should I use a reverse proxy like as shown and redirect traffic to my web server? Is this a more secure way instead of just opening rules at Firewall A and B and let traffic through? And why is it more secure?
thanks