To note before compiling the program I disabled ASLR via:
$ sudo -i
root@laptop:~# echo "0" > /proc/sys/kernel/randomize_va_space
root@laptop:~# exit
logout
I then compiled the program via:
gcc -ggdb -mpreferred-stack-boundary=4 -o test vuln.c
(I also didnt understand the -mpreferred-stack-boundary=4 parameter)
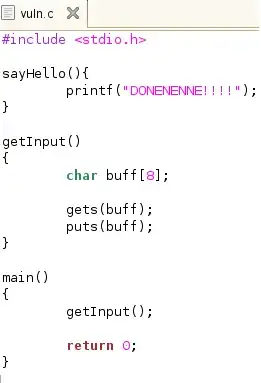
I have a program :
The overflow in theory should occur when the compiler gets to the line of gets(buff); where I have been attempting to overflow the return address ($RIP).
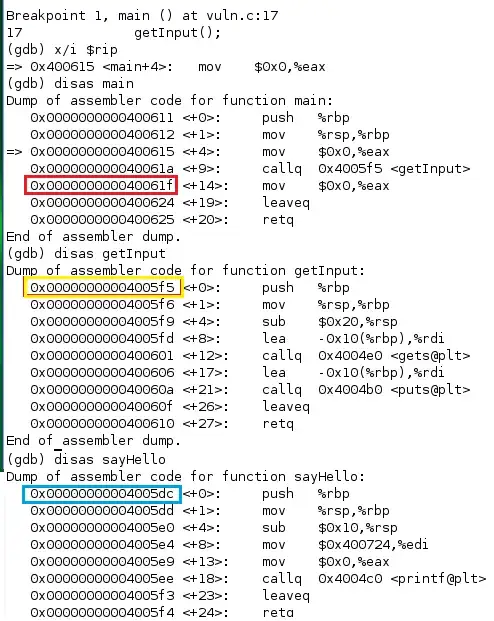
Below is the disassembly of my main method, getInput() and sayHello() (for the purpose of showing the address of the sayHello method, 0x4005d, which I hope to overwrite the stack RIP with).
When I give an input of above 15 x A's I segfault the program. And when I provide more than 24 x A's I begin to overwrite the $RIP, i.e. 25 x A's would make the RIP value 0x0000000000400041. Logically, I tried to then provide the hex values for "4005dc" (sayHello() address) however I fail when attempting that. When using online hex to text converters, the corresponding text value I get from "4005dc" is "@Ü".
More so I understand that when the program reached the retq instruction within getInput() it will pop the return address of the top of the stack and jump to it.