I was playing around with the security settings in my browser (IE) after being attacked by malware. I noticed an option to disable downloads. If I were to disable downloads, and re-enable them when necessary, would this provide more protection for my computer against malware (drive-by downloads) from websites?
2 Answers
Short answer: No. Useless.
Detailed answer:
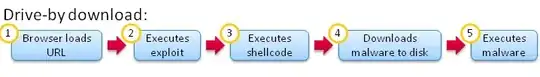
In fact, drive-by download attacks are malware delivery techniques a user may encounter by a simple visit of a website. This simple visit is what is referred to by drive-by download. It is an attack where the user is not intending to download anything at all.
A drive-by download attack may require or not user's interactions. It occurs without the user's consent and knowledge. It takes advantages of the vulnerabilities available in the browser itself as well as the ones available in its plugins or extensions.
Note that in case this attack requires the user's interaction, such interactions are performed most of the time -if not the only way- by clicking on some pop up windows: whether you click to agree (Ok), disagree (Cancel) or simply leave the window (X) you the attack will be triggered (sometimes you get a series of popup windows)
For instance, CVE-2011-0611 was a 0-day vulnerability up to April 13th, 2011 . It was used to infect the homepage of the Human Right Watch website in UK. The infected page contains a rogue <script src=newsvine.jp2></script> element. This tricks the browser into caching and executing newsvine.jp2 as JavaScript code. It was a drive-by cache attack which is just a case of drive-by download attacks. The caching is successful, but the file cannot be executed as JavaScript because it is actually a renamed malicious executable corresponding to a backdoor from the pincav family.
Another rogue script element found on the infected page is <script src="/includes/googlead.js"></script>, which unlike most drive-by download attacks, loads a local .js file. The JavaScript code in googlead.js creates an iframe that executes the SWF exploit from a domain controlled by the attackers.
We can mention also the famous and successful a drive-by download attack of which no browser was safe as long as they run a vulnerable version of JRE at that time (CVE-2011-3544) leading to thousands of visitors of the Amnesty International's homepage in UK were thus infected by Trojan Spy-XR malware. The attacks continued until June 2011, so later after you asked this question: Google Chrome was not safe of it.
On October 24th, 2013, the famous php.net website has been infecting its visitors by a drive-download attack through a hidden iframe tag.
How to avoid this type of attacks?
There are several ways to avoid such an attack, but they all generally result in a less usable experience on the internet. You can disable all JavaScript and embedded active content from running (or require prompts before they execute). This will prevent downloads without you having to approve the active script. Even the default options of recent browsers are a lot better than they used to be, but are not sufficient to stop all threats.
There isn't a perfect solution, you need to find the balance that works for you between usability and security. You may use some common sense: install only the browser plugins/extensions you really need; do not visit website where such attacks have more probability to be hosted (porn websites ...). If you want to visit such untrusted web sites then you should consider using more secure options or using a virtual machine to reduce your risk, but if you stay on the respectable parts of the Internet and keep your browser, AV and operating system all patched/up-to-date.
Nice question, but no. Drive-by-downloads exploit a flaw in either Javascript, Java, Flash, a PDF reader, or perhaps some insecure plugin you have installed.
If you're interested in protecting yourself from drive-by-downloads, you'll reduce your target area considerably if you were to use NoScript, uBlock Origin, and of course, by disabling Flash and Java.
I don't know if these are available for Internet Explorer, but they are available for Firefox, and Chrome has some equivalents. If you'd like to learn more about drive-by-downloads, read this OWASP document.
Here are some security options by browser:
Chrome
FireFox
Now why would we block ads? Because adservers become compromised on occasion, and can easily expose you to malware. Blocking these ads from even loading is very helpful.
Personally, I ALWAYS disable Java and Flash. There's next to no reason to use them at all in a secure environment, so I don't run them. Java and Flash both have a new exploit every second it seems, so it's really asking for trouble to use either of them while surfing the web.
I understand the need for Flash for websites such as youtube, but there's also an addon that creates a button in Firefox that lets you toggle flash. However, in FireFox, you can simply choose the option, "ask to activate," so you can decide whether or not flash gets activated on a website.
If you want to take security to the next level, you could also use Virtual Machines to isolate web browsing activities (I'd still use uBlock Origin, et al). For example, Oracle VM VirtualBox is pretty good for this.
The chances of someone creating malware that escapes the virtual machine is very low, much, much lower than someone getting hit by a drive-by-download. In fact, if there's an infection, there's a 99.99~% chance of them only infecting your virtual machine, while your host operating system remains intact.
- 22,498
- 8
- 74
- 91