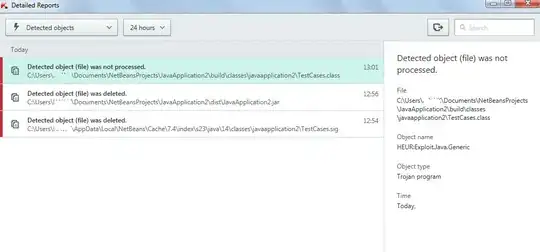
Just now I was testing a very simple code in Java when I noticed a strange thing. On compiling the program my antivirus detected it as trojan and deleted the jar file.
Further it is not allowing me to compile the program.
The above characteristic is not displayed on removing str.replaceAll() from the code.
Why is this happening?
What kind of exploit is it in Java and how can it be fixed?
Why using
str.replaceAll()specifically shows this kind of behavior?
My Java code is
public static void main(String args[])
{
String str="1000010111111010101010101001111110111010110101000001000000000000000000000000000000000000000000000000000"
+ "111111111111111110000000000000000000000000000000000000000000000000000000000000000";
System.out.println("String len="+str.length()+" No of ones= "+(str.length()-str.replaceAll("1", "").length()));
}