I have heard that using switches in my network helps prevent against a packet sniffing attack but how does it help prevent the attack?
-
Possible duplicate of [Preventing man in the middle attack](http://security.stackexchange.com/questions/9623/preventing-man-in-the-middle-attack) – StackzOfZtuff Oct 07 '15 at 11:55
3 Answers
By their function, a switch will only forward packets to the port where the destination computer (identified by it's MAC address) is. For this reason, they are said to mitigate sniffing attack.
However, switches are not security devices but network devices. In order to know where a specific computer is, they have to learn where they are. For this, they read the MAC address of computer in the different packets that goes through them. When possible they will assign MAC to a specific port and continue to forward traffic related to this MAC to this specific port only. Due to the protocol, you can take advantage of this by performing ARP poisoning, confusing the switch which ultimately will continue to operate as a simple hub, forwarding all traffic to all ports. With this attack, one can still perform sniffing.
-
ARP poisoning's intent is to attack a L3 ARP table; while this may have the side affect you describe depending on how it is performed, it isn't the intent of that type of attack. MAC address flooding is the type of attack that affects a L2 switch in the manner you describe. – YLearn Feb 18 '19 at 12:38
Short answer: Switches only help when upgrading from a hub, don't add it to your network unless you need it.
M'vy and GreatSeaSpider have given great answers!, I will try to simplify and show visually what they mean. It's all about collision domains! Image A explains what each device does, and Image B shows how that affects a network.
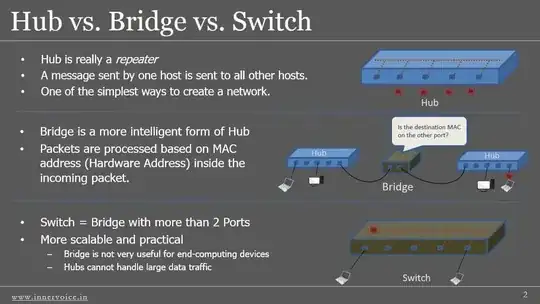
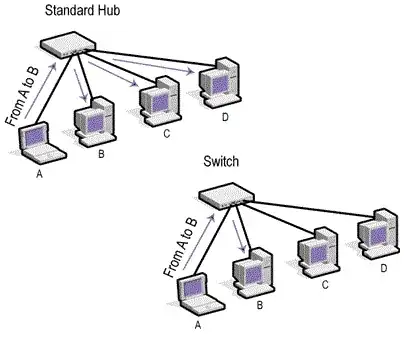
(source: networking-basics.net)
With a hub, any device in the CD (collision domain) can sniff packets sent by any other device in the CD. A switch stops that by only sending the packet to the appropriate device. Unmanaged switches are so cheap and perform so much better than hubs you would be better off doing this anyway.
If a switch doesn't know the destination device yet, or it's ARP table becomes overloaded by ARP spoofing, it will act like a hub and transmit to all devices
This is where port security comes in. The less frequently your network changes, the easier port security will be to set up. However to use it you need a managed switch, which is more expensive than a simple, unmanaged switch.
- 105
- 8
As M'vy has said switches are networking devices not security devices. It is however, worth noting that sniffing will be possible within each collision domain regardless of any attacks. That is to say that if you connect several devices to a single switch port (perhaps by using a hub), then the switch has to forward all traffic for all of those devices to that port. Therefore all of the traffic sent to any of those devices will be visible to all of those devices.
It's also worth noting that some switches do provide additional security features designed to help mitigate several types of attack, such as ARP poisioning/flooding/spoofing and rogue DHCP servers (vectors which allow packet interception or packet sniffing). A couple of the the most useful security features are port security, and DHCP snooping.
Port security basically means that the number of MAC addresses allowed on each switch port is limited, and the switch can be given a list of fixed MAC addresses in addition to those learned by the switch. DHCP snooping attempts to prevent any DHCP responses from unauthorised DCHP servers, and to try and ensure that each host only uses the IP addresses assigned to them by DHCP.
Milage per vendor will vary, and of course there's overhead involved in configuring and maintaining any additional features like the above.
- 2,054
- 16
- 14