I know the general concept of how digital certificates works: e.g. server "signs" the message it wants to send to the client using his private key and sends along a message digest and on the receiving side client KNOWS the server public key and can verify that the message is indeed authentic (comes from server and not modified in transit) by using a decryption function and looking over the content of the message, do it's digest also and confirm that the actual message received is authentic.
The question is how can client tell that the server public key sent in the clear (I guess it's sent in the server hello response) is authentic ? I can understand that large CA have their certificates already installed on the client machine but if the server sends a certificate signed for example by Digicert how can I tell on client that that is indeed the case (maybe a MIM intercepted ssl handshake changing things) ?
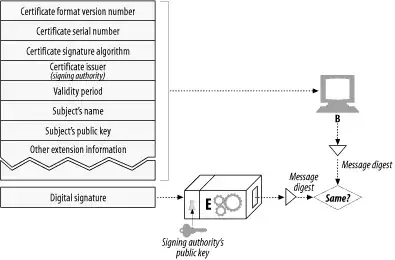
To clarify things I've added the picture that describes the process by which client verifies that certificate signature is real. "When the browser receives the certificate, it checks the signing authority.If it is a public, well-respected signing authority, the browser will already know its public key (browsers ship with certificates of many signing authorities preinstalled), so it can verify the signature" Question: Signing authority public key has to be communicated somehow to the client (even if that CA is stored locally, how do you know what origin server uses ?). How is that process done ?