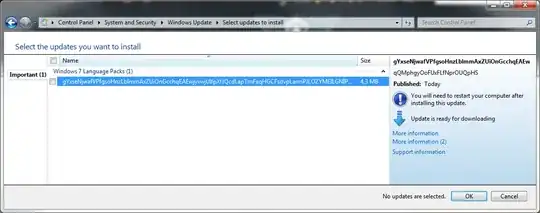
This morning, I noticed that a new Windows update was offered to me. It looks very suspicious to me:
Here are the update details:
gYxseNjwafVPfgsoHnzLblmmAxZUiOnGcchqEAEwjyxwjUIfpXfJQcdLapTmFaqHGCFsdvpLarmPJLOZYMEILGNIPwNOgEazuBVJcyVjBRL
Download size: 4,3 MB
You may need to restart your computer for this update to take effect.
Update type: Important
qQMphgyOoFUxFLfNprOUQpHS
More information:
https://hckSLpGtvi.PguhWDz.fuVOl.gov
https://jNt.JFnFA.Jigf.xnzMQAFnZ.edu
Help and Support:
https://IIKaR.ktBDARxd.plepVV.PGetGeG.lfIYQIHCN.mil
Obviously, this seems way too fishy to install, but I would like to know more. Has everyone received this update (Google only has a couple of hits for this)? Could this be an attack? Is there a way to download the update data without installing it?
I'm open to any ideas.
I'm running an Windows 7 Pro (64-bit).
As @Buck pointed out below, the update is no longer available through Windows Update. I'm not sure how this question will be resolved.