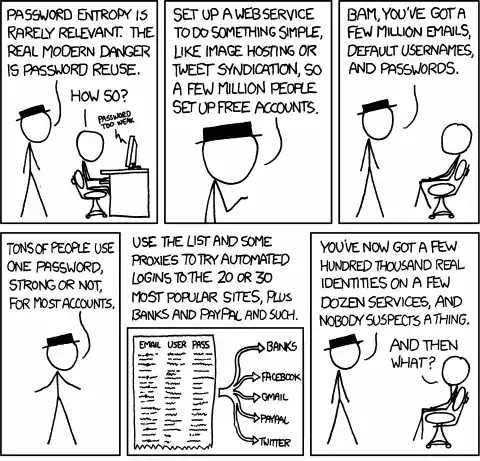
Having a strong password does not protect you from vulnerabilities relating to password reuse.
So you've come up with a strong password that you use to sign up to most internet services you use. Great! You are now probably safe from people who are trying to log into your specific account by guessing every possible password you could have and hoping that one of them is correct (a "brute force" attack).
Let's say you come across my brand new website, that offers you some wonderful newsletter you're really interested in. You make the decision to sign up to this site. You enter your email address, and your usual strong password.
Unfortunately for you, I haven't been exactly honest, and while I will set up a newsletter subscription for you, I'm also sending the email address and password you just typed in to my personal email. Once that arrives in my inbox, I can try the combination on facebook, gmail, yahoo mail, twitter, etc etc. Sooner or later I'm going to get into one of your accounts.
Alternatively, suppose I was honest and wasn't out to steal your account, but I was just really bad at security. Maybe I was storing your password in a database in plain text, and didn't have anything in place to stop an attacker from getting into it. So, one day along comes a nasty person who finds a way to copy the contents of the database, and suddenly he has your email and password too! Oops.
When you choose a password for any website or service, it's always best to assume that the password could, at some point, be read by someone.
You just need to make sure that if and when that happens, the information that is compromised does not let anyone into any of your other accounts.