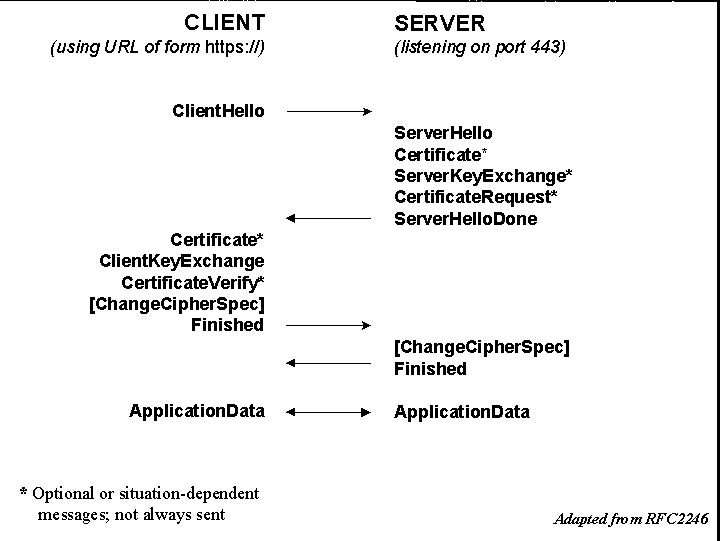
As far as I understand after reading this beautifully explained answer, MiTM data injection attacks via client-initiated renegotiation can only happens if the attacker is already in a connection with the server which did not check his credential. He then issues a command, and escalates his privilege by triggering a renegotiation and splicing in an authentic client's handshake, and the server will then mistake the command for one coming from an authentic client.
Similarly, according to this post, the DoS attack works by an attacker first establishing a connection to a server (during which his credential is not checked), and then repeatedly trigger renegotiation on the same connection.
My question is: if I'm operating in an environment where the client's certificate is checked upon first connection, I should not be affected by this, is it correct?
A related question: if the connection is started after StartTLS, since StartTLS checks for client's certificate, are client-initiated renegotiation attacks also not applicable?
](../../images/3831630995.webp)