I have a problem with the Nikto Web Scanner.
I would like to scan a site but Nikto returned the response with a HTTP 403 status code:

After that I tried to change the USERAGENT in nikto.conf. Nikto is now able to return with HTTP 200 status code for first few requests. But the following requests are returning with HTTP 404 status codes (not returning any status codes after that):

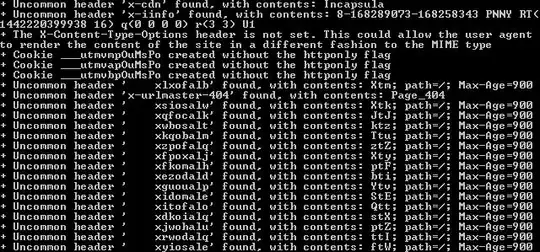
The following shows the Nikto scan result:
What exactly is happening in between? How can I get a normal scan using Nikto?